1 . Introduction
2 . My Setup
3 . What is Sherlock?
4 . Why use Sherlock?
5 . How to use Sherlock?
6 . Summary
This post is designed to introduce you to the tool Sherlock.
1. Introduction
Welcome to the fifty-fifth blog post of 100 tools in 100 days.
Find Sherlock @ GitHub here.
Sherlock was created by Siddharth Dushantha and you can find his respective sites below:
GitHub
LinkedIn
Medium
2. My Setup
For running the Sherlock tool, I used Kali Linux in a VMware Workstation 16 Player virtualized environment.
3. What is Sherlock?
Sherlock is another social media username collector, similar to Blackbird and Maigret.
4. Why use Sherlock?
Sherlock may be a viable option if you wanted to compare findings amongst your other username search tools. Additionally, Sherlock’s site list is regularly updated with the latest file updated 27 days ago. Today you can use Sherlock to search 355 different platforms.
5. How to use Sherlock?
Step 1:
Create a python virtual environment by entering the following:
python3 -m venv sherlock
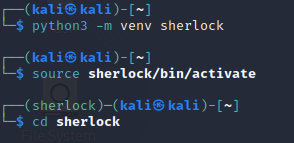
Step 2:
Load the python3 virtual environment by entering:
source /sherlock/bin/activate

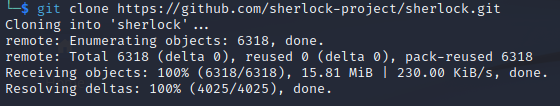
Step 3:
Clone the Sherlock repository by entering the following command:
git clone https://github.com/sherlock-project/sherlock.git
Step 4:
Change your directory into the downloaded repository by entering the following command:
cd sherlock
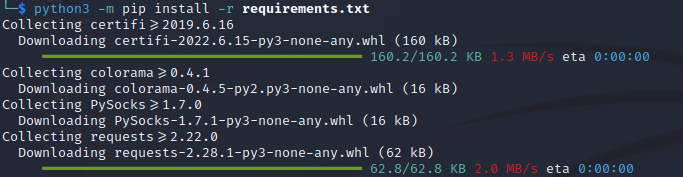
Step 5:
Install Sherlock using the following command:
python3 -m pip install -r requirements.txt
Step 6:
Verify Sherlock installed by entering the following command:
python3 sherlock --help
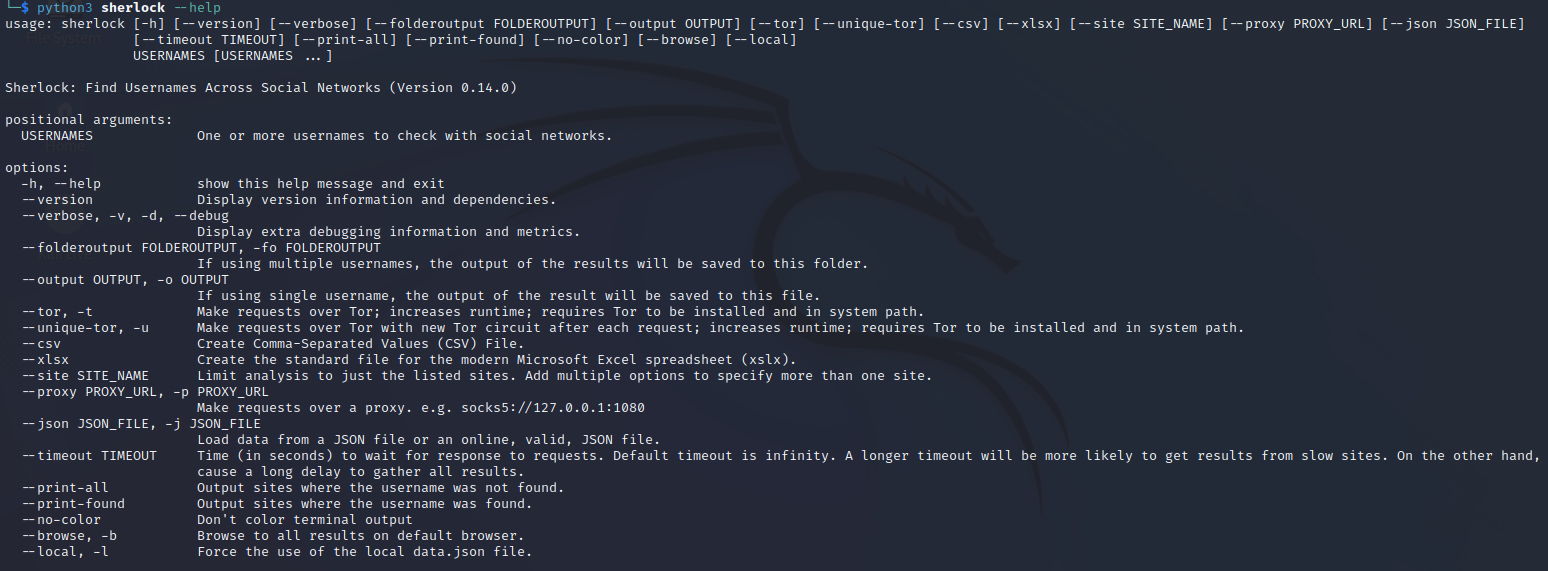
Step 7:
Search for a username using the following command:
python3 sherlock <USERNAME>
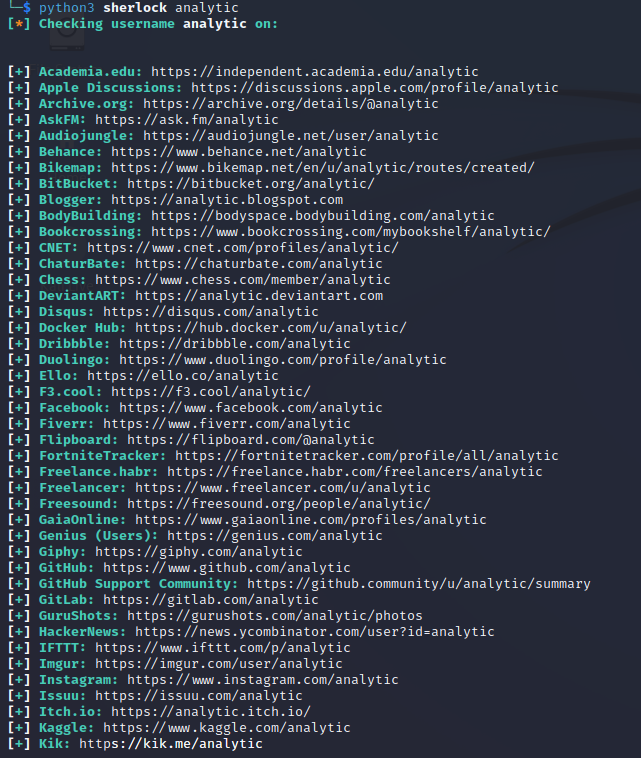
Step 8:
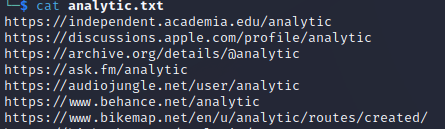
Sherlock also can output files, display only found names, and create CSV
files for further analysis by entering the following options:
python3 sherlock <USERNAME> -o <FILENAME> --csv --print-found --verbose
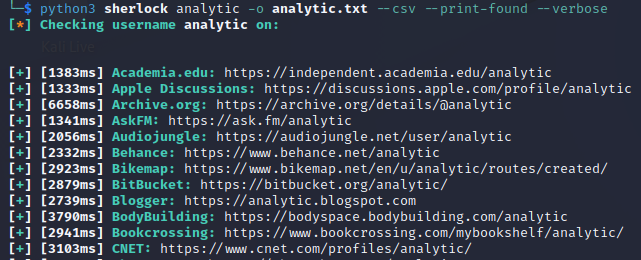
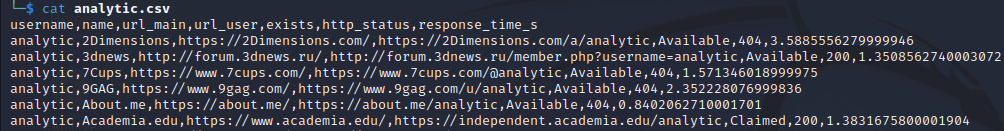
6. Summary
Hopefully Sherlock can be an option for finding usernames during your OSINT / exploitation attempts. This tool offers ease of use, a simple output feature and a CSV output option for further analysis.
I hope you enjoyed this blog post.
Thanks for reading!
If you have suggestions for what tool to cover next, contact me!