1 . Introduction
2 . My Setup
3 . What is Sublist3r?
4 . Why use Sublist3r?
5 . How to use Sublist3r?
6 . Summary
This post is designed to introduce you to the tool Sublist3r.

1. Introduction
Welcome to the forty-seventh blog post of 100 tools in 100 days.
Find Sublist3r @ GitHub here.
Sublist3r was created by Ahmed Aboul-Ela find him on LinkedIn here.
2. My Setup
For running the Sublist3r tool, I used Kali Linux in a VMware Workstation 16 Player virtualized environment.
3. What is Sublist3r?
Sublist3r is an OSINT tool used to enumerate subdomains. Sublist3r uses a few different search engines to discover subdomains on your behalf.
4. Why use Sublist3r?
During the OSINT gathering aspect of penetration testing, an analyst may gather all possible subdomains of an organization. Since Sublist3r uses search engines for discovering subdomains this is considered a passive OSINT reconnaissance.
5. How to use Sublist3r?
In order to use Sublist3r, you must have the dependency python3-pip installed to install Sublist3r, find instructions on installing pip here.
You must have a VirusTotal API key which can be found here.
You will need to download a forked and fixed version of the python file in step 2.
Step 1:
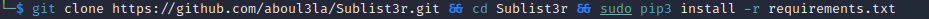
Install Sublist3r by entering the following command in your terminal:
git clone https://github.com/aboul3la/Sublist3r.git && cd Sublist3r && pip3 install -r requirements.txt
This command will clone the GitHub repository where Sublist3r resides, change the directory into that cloned repository and install Sublist3r.
Note: The current version of Sublist3r searches VirusTotal, in order for this function to work we need to download a fixed version of the python script and add the VirusTotal API to our environment when running sublist3r.
Step 2:
In the directory from step 1 enter the following
command in your terminal:
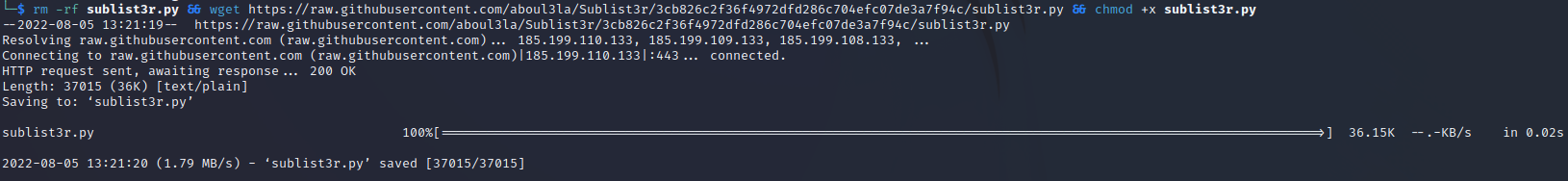
rm -rf sublist3r.py && wget https://raw.githubusercontent.com/aboul3la/Sublist3r/3cb826c2f36f4972dfd286c704efc07de3a7f94c/sublist3r.py && chmod +x sublist3r.py
This should have downloaded a new version of sublist3r.py while also removing the old version and giving the new version executable permissions.
Step 3:
Enter the following command to export the virus total API key:
export VT_APIKEY=YOUR_CUSTOM_API_KEY_HERE

Step 4:
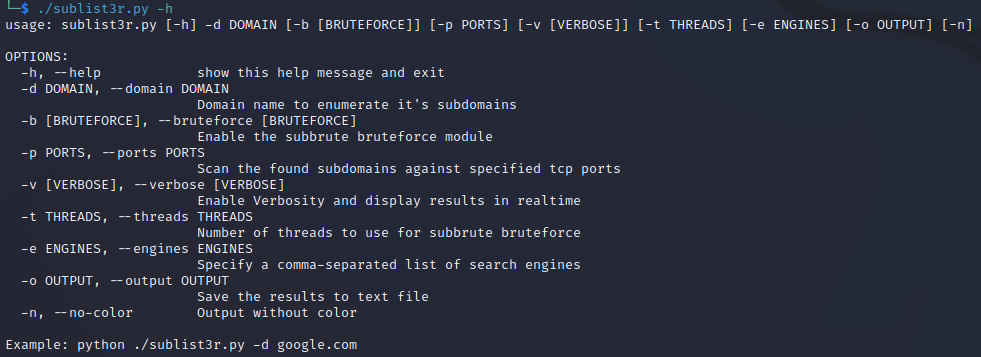
Check out the help page by entering the following command:
./sublist3r.py -h
Step 5:
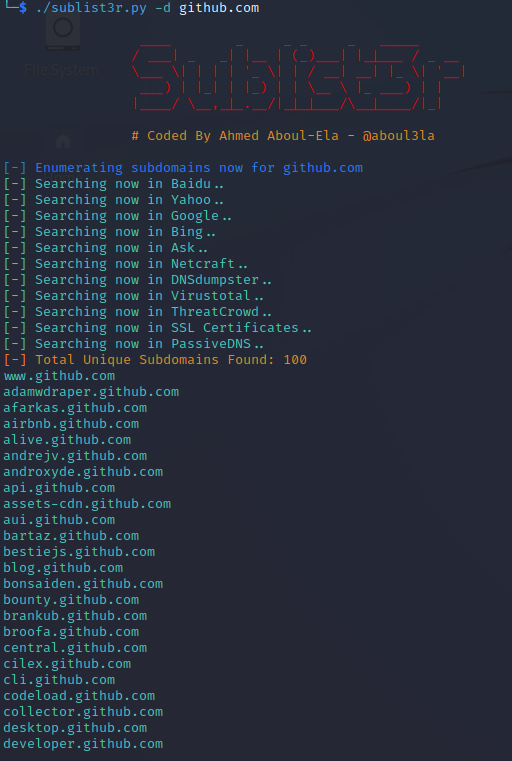
Search for subdomains using Sublist3r by entering the following command:
./sublist3r.py -d github.com
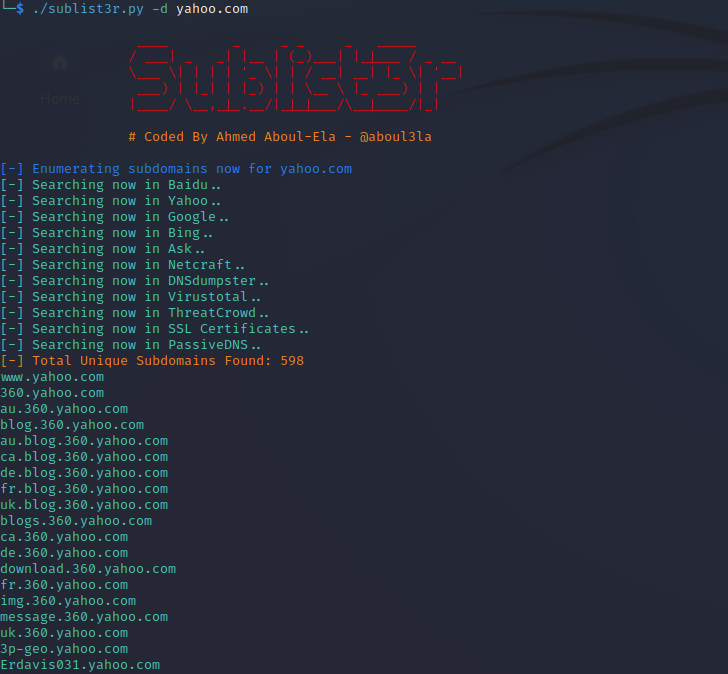
Note: currently you need to export the Virus Total API key before running Sublist3r in a new terminal window. You can add the API key to your bash script by following the advice found here.
6. Summary
Sublist3r is a useful OSINT tool for discovering the Subdomains of an organization. Penetration testers may use Sublist3r when finding avenues of approach for reconnaissance and future attacks.
I hope you enjoyed this blog post.
Thanks for reading!
If you have suggestions for what tool to cover next, contact me!