1 . Introduction
2 . My Setup
3 . What is RustScan?
4 . Why use RustScan?
5 . How to use RustScan?
6 . Summary
This post is designed to introduce you to the tool RustScan.

1. Introduction
Welcome to the forty-fourth blog post of 100 tools in 100 days.
Today features another tool created by Bee Skerritt, and 25 other contributor’s who dedicate their time and knowledge to making RustScan what it is today.
Find RustScan @ GitHub here.
Find Bee Skerritt at:
GitHub
LinkedIn
Personal Blog
2. My Setup
For running the RustScan tool, I used Kali Linux in a VMware Workstation 16 Player virtualized environment.
For my vulnerable host, I am using the Metasploitable 2 instance running in a VMWare Workstation 16 Player virtualized environment.
3. What is RustScan?
RustScan is one of the fastest port scanners available.
RustScan allows scripting support, stealth support for evading detection, and adaptive learning to tailor itself to the environment and user.
4. Why use RustScan?
Security researchers and testers often use other port scanning tools to discover whether a port is open, closed, or unresponsive, and then the scanner tests those ports. Determining which ports are open can take some scanners a lot of time. RustScan bridges that gap and scans 3,000 ports per second and then feeds that information automatically to Nmap to discover hosts, services, run scripts, etc on the host.
5. How to use RustScan?
I am using RustScan with Docker. If you are on Kali Linux and you do not have Docker installed please follow this guide first.
Step 1:
Using RustScan is easy with Docker and only takes a moment to set up.
In your terminal enter the following command:
wget https://github.com/RustScan/RustScan/releases/download/2.0.1/rustscan_2.0.1_amd64.deb
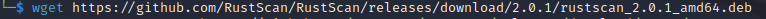
Step 2:
Use the Debian package manager to install the .deb file from step 1 by
entering the following command:
sudo dpkg -i rustscan_2.0.1_amd64.deb
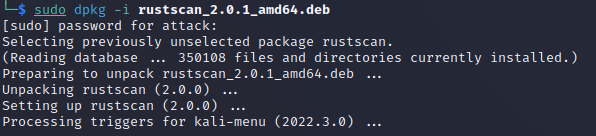
Step 3:
Enter the following command to view the RustScan help page:
rustscan --help
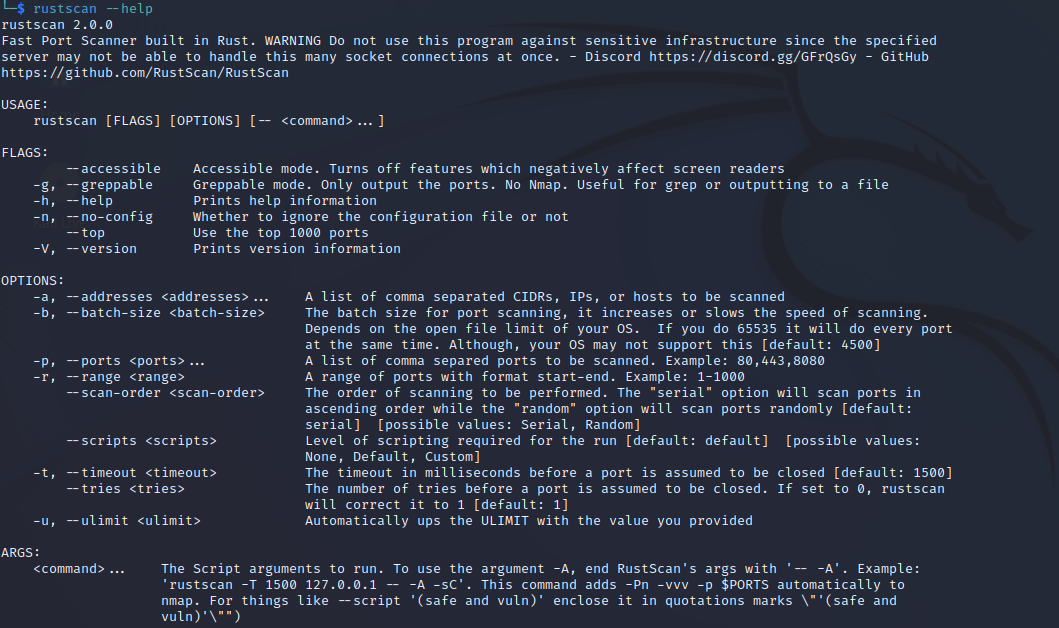
Step 4:
Use RustScan by entering the following command:
rustscan -a <HOST>
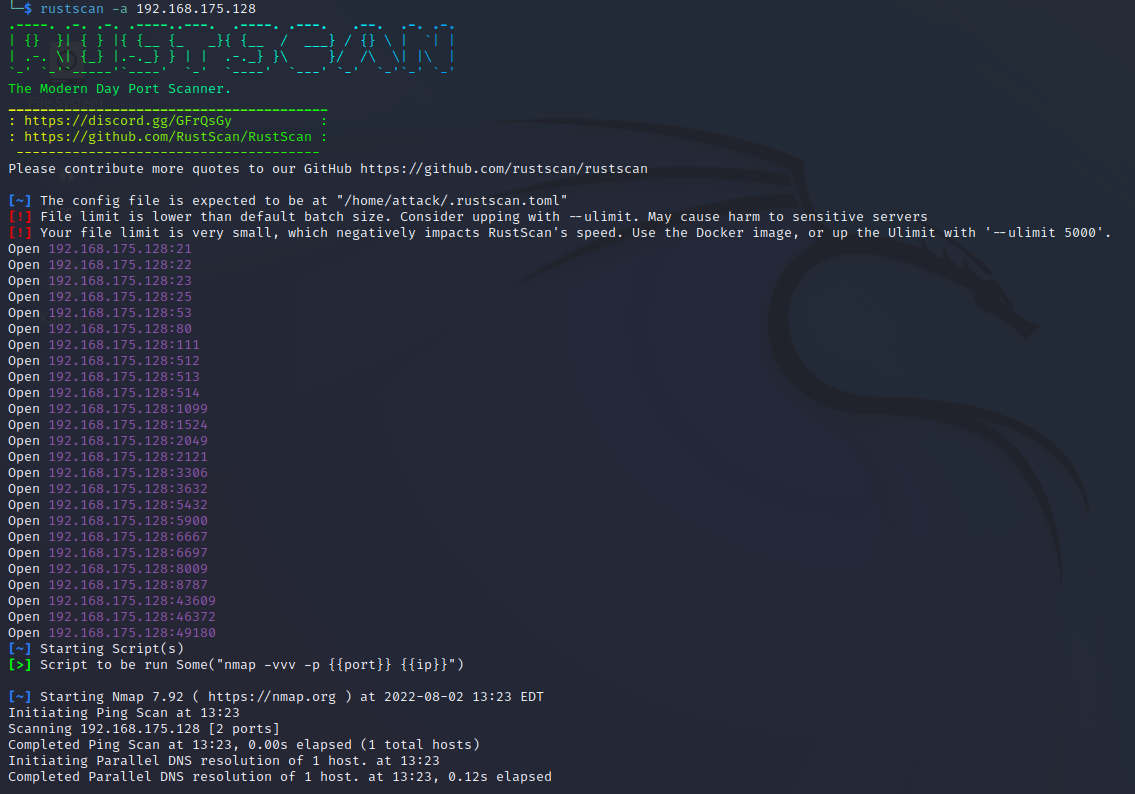
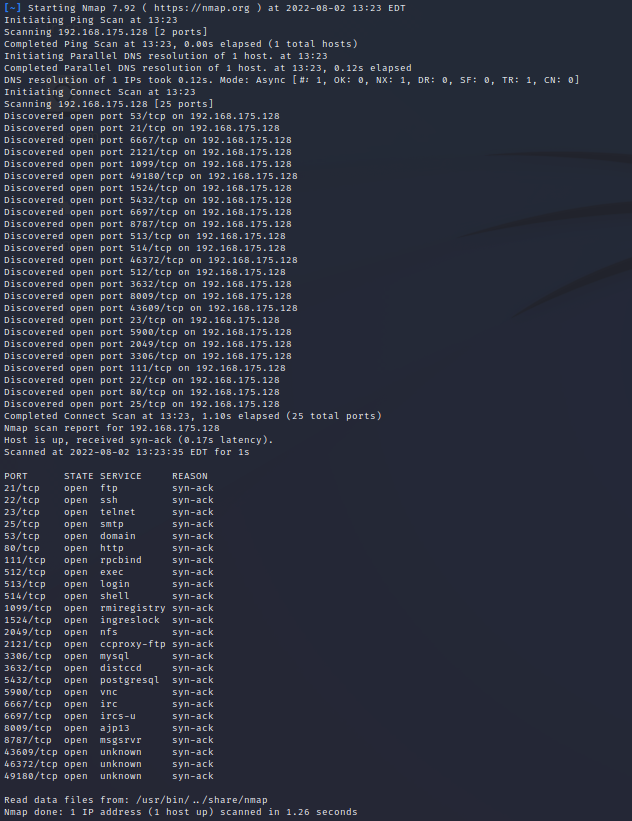
RustScan found these open ports on my Metasploitable2 instance in less than 15 seconds.
Note, while RustScan is extremely fast and useful I do get different results every time I scan a host. Some of the ports identified as open are not actually opened and some of the open ports are not being found as open. So please use RustScan with other tools to complete a full analysis of available ports.
6. Summary
RustScan is a fast and easy to use port scanner that detects open ports in seconds. With this information, you could perform further testing to verify the ports found and discover if the ports have vulnerable services running.
I hope you enjoyed this blog post.
Thanks for reading!
If you have suggestions for what tool to cover next, contact me!