1 . Introduction
2 . My Setup
3 . What is Scanless?
4 . Why use Scanless?
5 . How to use Scanless?
6 . Summary
This post is designed to introduce you to the tool Scanless.
1. Introduction
Welcome to the fortieth blog post of 100 tools in 100 days.
Find Scanless @ GitHub here.
Find Austin Jackson on LinkedIn here.
2. My Setup
For running the Scanless tool, I used Kali Linux in a VMware Workstation 16 Player virtualized environment.
For the website I am scanning I am using the example Austin used in the Scanless demonstration scanme.nmap.org.
3. What is Scanless?
Scanless is a tool that allows for port scanning of hosts using websites to perform those scans instead of your own device.
4. Why use Scanless?
Scanless is great for penetration testers that do not want to be identified by IDS / IPS systems on the target network.
A developer or security researcher may use Scanless to perform external port scans to see what is open and available on the internet for the hosts they manage.
5. How to use Scanless?
Step 1:
To install scanless on your Linux device open a terminal window and enter the following command:
pip install scanless --user
If you are not signed in as root you may have installed scanless in a directory that is not on your environment path.
If you saw the below image at the end of installation continue to part 2.
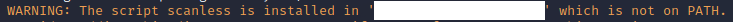
Step 2 (optional):
You need to add the directory path where scanless is installed to your environment variables.
Enter the following command:
export PATH="path/from/end/of/scanless/install"

Step 3:
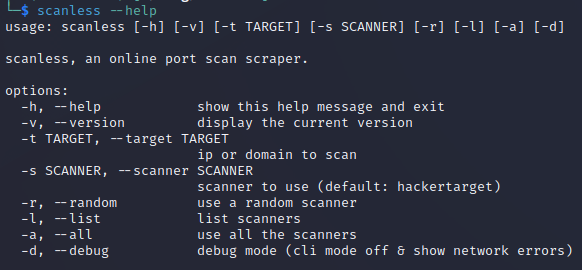
Check out the Scanless help page to understand the command and options.
scanless --help
Step 4:
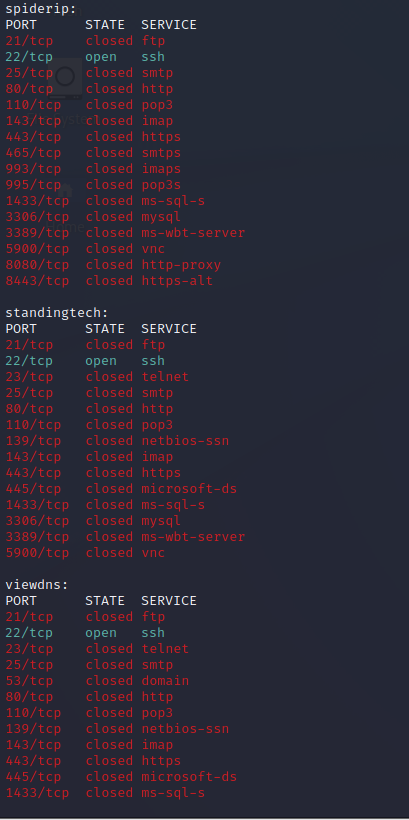
In this next step, I will perform a scan on scanme.nmap.org using the -a (for all scanners) option.
scanless -t scanme.nmap.org -a
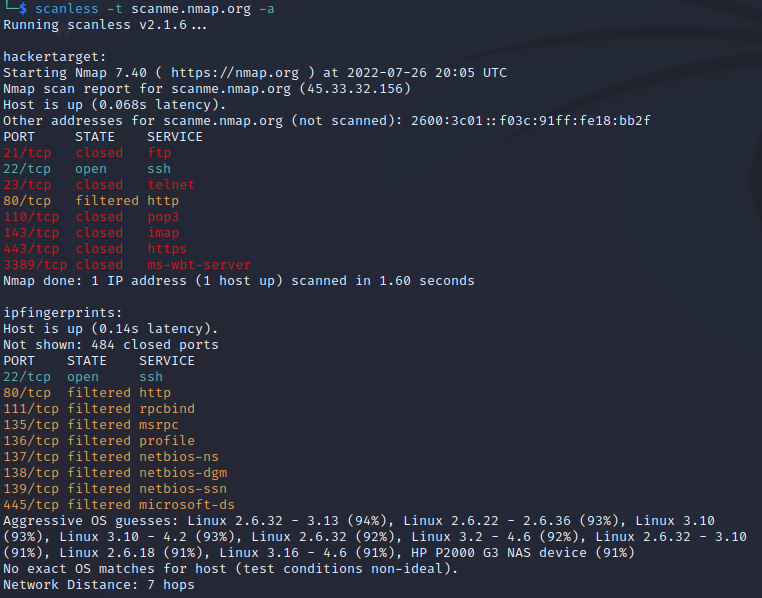
From the results, we see that hackertarget identified port 22 as open and port 80 as filtered. While ipfingerprints identified many other ports filtered.
The other scanners returned results of only port 22 as open.
6. Summary
If you need to perform a port scan and do not want the scan to originate from your device, using scanless is a simple tool to facilitate scanning from online scanning sites.
I hope you enjoyed this blog post.
Thanks for reading!
If you have suggestions for what tool to cover next, contact me!