1 . Introduction
2 . My Setup
3 . What is Kerbrute?
4 . Why use Kerbrute?
5 . How to use Kerbrute?
6 . Summary
This post is designed to introduce you to the tool Kerbrute.
![]()
1. Introduction
Welcome to the thirty-second blog post of 100 tools in 100 days.
Find Kerbrute here.
Ronnie Flathers created Kerbrute, and a bunch of other cool tools you will see in future posts.
Find Ronnie Flathers here:
GitHub
LinkedIn
Twitter
Slightly Outdated Blog Site
2. My Setup
For running the Kerbrute tool, I used Kali Linux in a VMware Workstation 16 Player virtualized environment.
For a vulnerable Active Directory environment, I am using the Attacktive Directory room on Try Hack Me located here.
3. What is Kerbrute?
Kerbrute is a tool written in the Go language that enumerates users, brute forces passwords, and allows for password spraying attacks through Kerberos Pre-Authentication in an Active Directory environment.
Today we are going to use Kerberos only for username enumeration. Attacking and gaining access to the Active Directory environment will require the use of Impacket, Bloodhound, and Neo4j which will be tools discussed in later series of this blog.
4. Why use Kerbrute?
You need to find usernames for a domain controller that you are attempting to access.
You need to test passwords against usernames that you found for a domain controller.
Kerbrute can be used by penetration testers to find access into an Active Directory environment.
Additionally, an internal security tester can verify and understand what information is accessible if Kerbrute was used against the network.
5. How to use Kerbrute?
Kerbrute is written in the Go language and we are going to use Go to install it. If you do not know how to make this work, check out yesterday’s blog post on waybackurls where I give a detailed explanation of installing Go, setting up Go, and installing packages from GitHub using Go. Yesterdays Blog Post.
Step 1:
Using Go install Kerbrute with the following command:
go install github.com/ropnop/kerbrute@latest
Step 2:
To see the help menu for Kerbrute enter the following command:
kerbrute -h
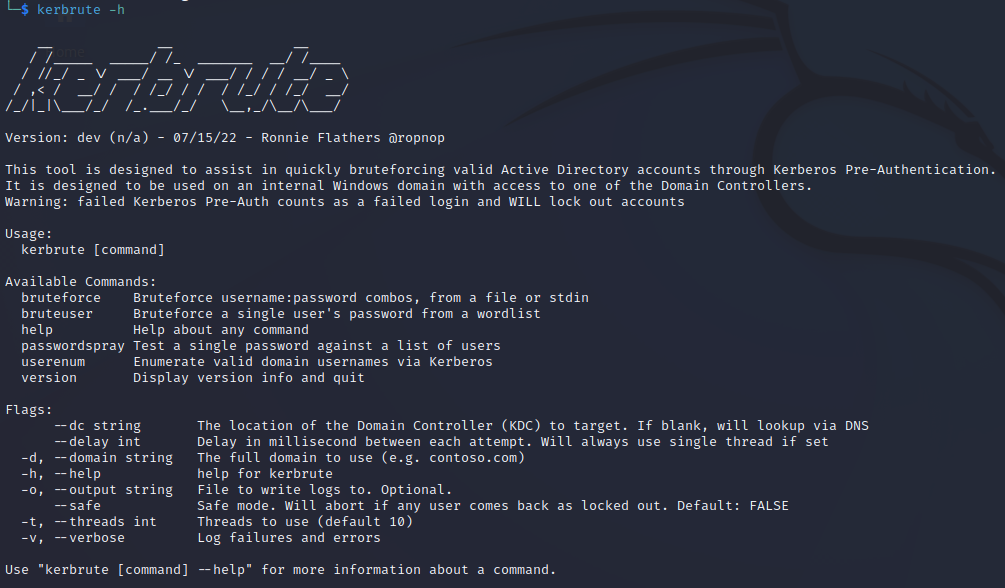
Our objective today is simple, enumerate users from the domain using a username wordlist. The wordlist used is the one provided in the Try Hack Me room.
Step 3:
Type the following command to enumerate users using Kerbrute:
kerbrute userenum --dc 10.10.22.158 -d spookysec.local userlist.txt
--dc is specifying the domain controller
-d is the full domain
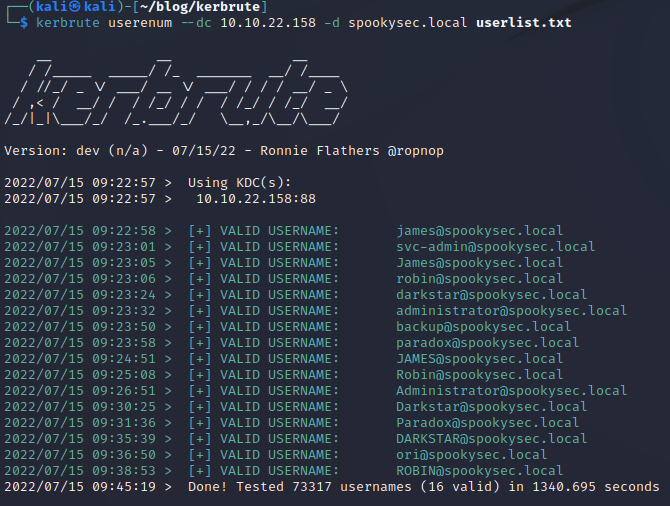
From the results, we can see that many user accounts were discovered. The majority of the user enumeration took less than 5 minutes, however, running the tool for the entire wordlist provided did take 23 minutes.
With this information, you could move forward and perform various password attacks.
6. Summary
Kerbrute is a pre-authentication Kerberos attack tool designed to enumerate usernames and perform bruteforce password attacks.
Kerbrute is just one of the steps in gaining access to Active Directory environments. Stay tuned for later blogs where I will discuss Impackets, Bloodhound, and Neo4j.
I hope you enjoyed this blog post.
Thanks for reading!
If you have suggestions for what tool to cover next, contact me!