1 . Introduction
2 . My Setup
3 . What is SecLists?
4 . Why use SecLists?
5 . How to use SecLists?
6 . Summary
This post is designed to introduce you to the resource SecLists.

Disclaimer : Please only use SecLists for professional and educational reasons. Do not use this resource for nefarious or malicious reasons.
1. Introduction
Welcome to the twenty-ninth blog post of 100 tools in 100 days.
Today will be a lighter post and involve a resource that can supplement many of the tools we have covered as well as many tools you may use.
Find SecLists here.
SecLists is maintained by Daniel Miessler, Jason Haddiz, and g0tmi1k on GitHub.
2. My Setup
For accessing the SecLists resource, I used Kali Linux in a VMware Workstation 16 Player virtualized environment. However, most of these lists are in .txt format so they can be used on nearly any device.
3. What is SecLists?
SecLists is a repository of lists used during directory discovery, web fuzzing, password spraying, web testing, URL discovery, username discovery, password discovery, and many other uses.
4. Why use SecLists?
SecLists is a one-stop-shop for all of your wordlist needs.
When you think of SecLists I want you to think “rockyou.txt” but for everything.
SecLists wordlists are divided into directory categories for ease of use.
5. How to use SecLists?
Getting access to SecLists is super easy.
Option 1 (Individual Lists):
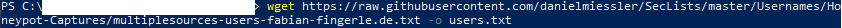
If you want to download individual lists then browse through the GitHub repository and find one that fits your needs and then grab it with wget, like this:
wget raw.githubusercontent.com/path/to/file -o filename.txt
You can view the raw URL of a file by clicking the “Raw” button and copying the URL into your wget command.
Also, remember wget can be used on Windows in PowerShell.
Option 2 (Entire Repository):
You can use the git clone command to clone the entire repository into your directory.
git clone https://github.com/danielmiessler/SecLists.git
Option 3 (Via Kali):
If you really want to do things the easy way, you can use apt in Kali Linux to download SecLists.
sudo apt install seclists
Note:
I believe that using apt will default SecLists to usr/share/seclists.
If you wanted SecLists in /usr/share/wordlists/seclists then you would need to move the directory.
6. Summary
SecLists is a great companion to any web fuzzing, directory discovery, username and password discovery, or other tools that use wordlists.
I highly suggest you keep SecLists as one of the wordlists you reference regularly for discovery.
I hope you enjoyed this blog post.
Thanks for reading!
If you have suggestions for what tool to cover next, contact me!