1 . Introduction
2 . My Setup
3 . What is Gobuster?
4 . Why use Gobuster?
5 . How to use Gobuster?
6 . Summary
This post is designed to introduce you to the tool Gobuster.
1. Introduction
Welcome to the twenty-third blog post of 100 tools in 100 days.
Find Gobuster here.
2. My Setup
For running the Gobuster tool, I used Kali Linux in a VMware Workstation 16 Player virtualized environment.
For my vulnerable host, I am using the Metasploitable 2 instance running in a VMWare Workstation 16 Player virtualized environment.
3. What is Gobuster?
Gobuster is another enumeration and web scanning tool for finding DNS names, IP addresses, directories, S3 buckets, and more for a given domain, IP address, etc.
I am going to use Gobuster today to find directories on the DVWA of Metasploitable 2 instance.
4. Why use Gobuster?
I like to use GoBuster as a fast alternative to tools like Dirbuster or Dirb.
Gobuster scans take seconds to minutes while Dirbuster often fails or takes so long that I cancel the scan.
Dirb is a great directory enumeration tool that does thorough scans, I talked about Dirb here on day 6!
5. How to use Gobuster?
Step 1:
Gobuster is fairly simple to use.
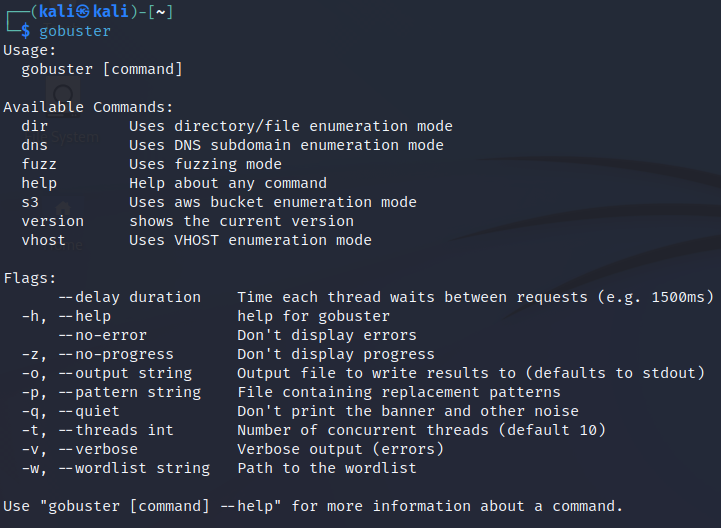
To see the help options just type gobuster in your terminal:
gobuster
To see help on a specific mode type:
gobuster help <mode>
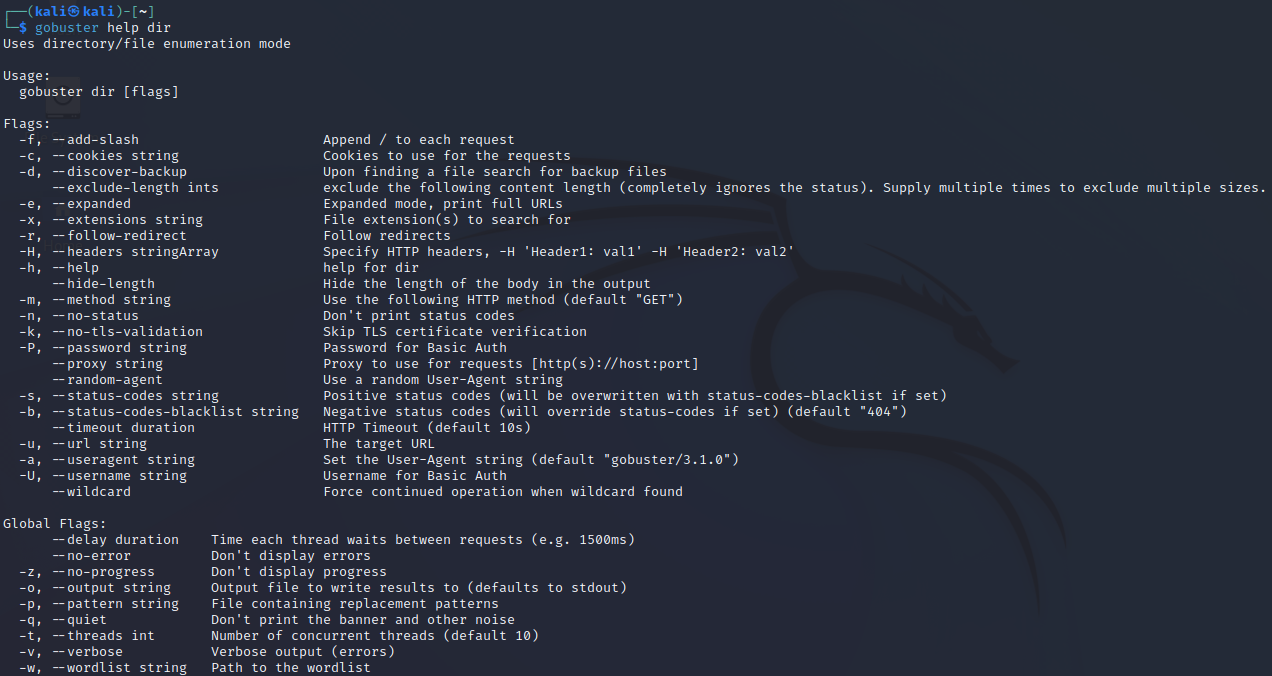
gobuster help dir
Step 2:
I am going to scan the web server on Metasploitable 2.
The command for Gobuster is fairly simple despite its length.
Use the following command:
gobuster dir -u http://192.168.175.128 -w /usr/share/wordlists/dirbuster/directory-list-2.3-medium.txt -o gobuster/initial -e
dir = directory mode
-u = specifying the URL to scan
-w = wordlist to use for scanning
-o = I output the file to a directory named gobuster and named the file initial
-e = show the full URL path of found directories
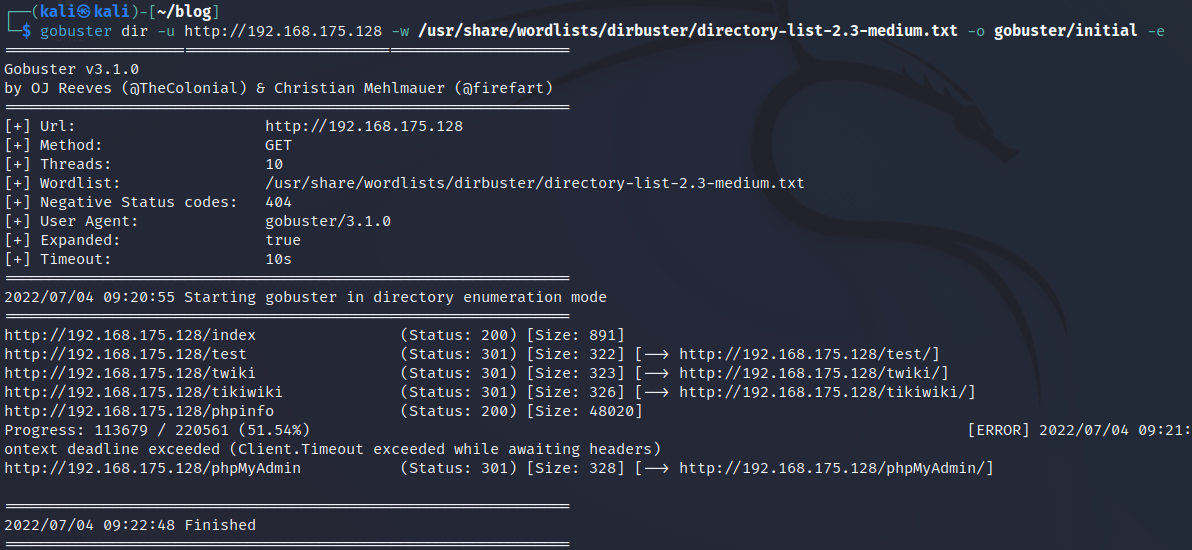
Anyone familiar with DVWA and Metasploitable 2 knows that there is a page named < IP Address >/DVWA and from our results, we see that Gobuster did not find it, this is because DVWA is not in my wordlist file.
6. Summary
Gobuster is a fast and easy to use tool for scanning websites for directories, DNS, S3 buckets, and other options.
I like to use Gobuster side by side with some of the other directory discovery tools like Dirb or even Dirbuster.
I hope you enjoyed this post and can use Gobuster in your future!
Thanks for reading!
If you have suggestions for what tool to cover next, contact me!