1 . Introduction
2 . My Setup
3 . What is enum4linux?
4 . Why use enum4linux?
5 . How to use enum4linux?
6 . Summary
This post is designed to introduce you to the tool enum4linux.

1. Introduction
Welcome to the twenty-first blog post of 100 tools in 100 days.
Find enum4linux here.
or at the GitHub here
2. My Setup
For running the enum4linux tool, I used Kali Linux in a VMware Workstation 16 Player virtualized environment.
For my Samba host, I am using the Metasploitable 2 instance running in a VMWare Workstation 16 Player virtualized environment.
3. What is enum4linux?
enum4linux is a tool that enumerates the data from Windows and Samba hosts running Server Message Block (SMB) services.
SMB usually runs on ports 139 and 445 on a host.
SMB provides users with shared access to files, printers, and other devices on a network.
4. Why use enum4linux?
enum4linux can help a penetration tester or developer determine SMB services on a device or network.
Information obtained from enum4linux can be used to access and compromise a system or even pivot into a different part of the network (if confidential information is shared within the SMB service).
Running SMB services is not always a bad thing, but misconfiguration of SMB can certainly leave a hole in security for an attacker to target.
5. How to use enum4linux?
enum4linux is really easy to use and comes pre-installed on Kali Linux.
Step 1:
To access the help menu for enum4linux type:
enum4linux -h
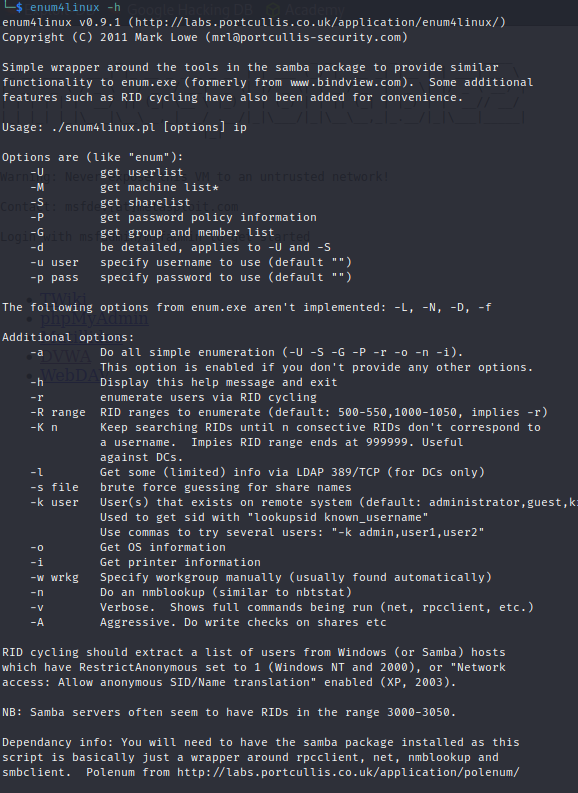
Step 2:
Using enum4linux on an IP address is simple.
If you want to scan for all simple enumeration methods you can use the command:
enum4linux <ip_address>
This is the same as:
enum4linux -a <ip_address>
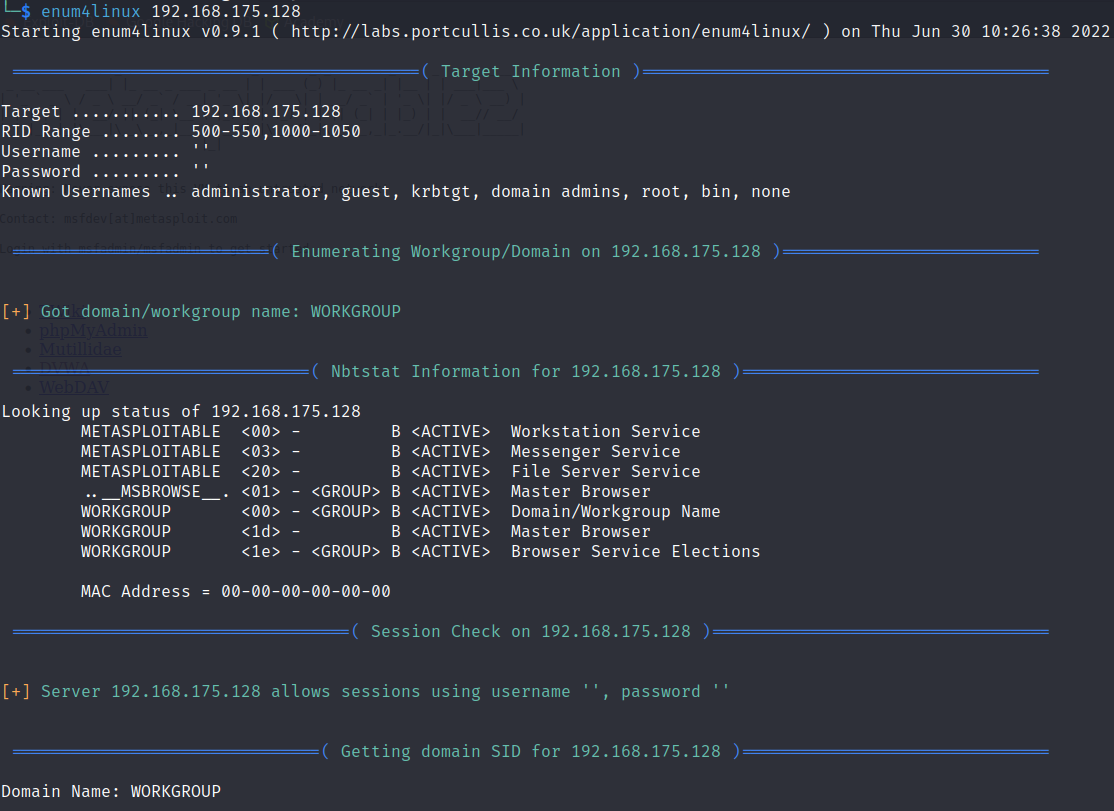
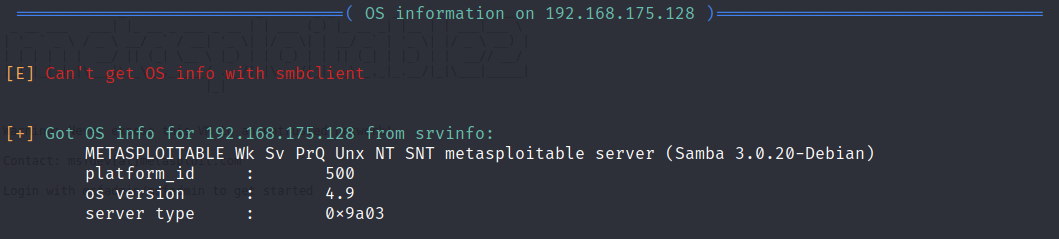
As you can see below enum4linux gave us the operating system information.
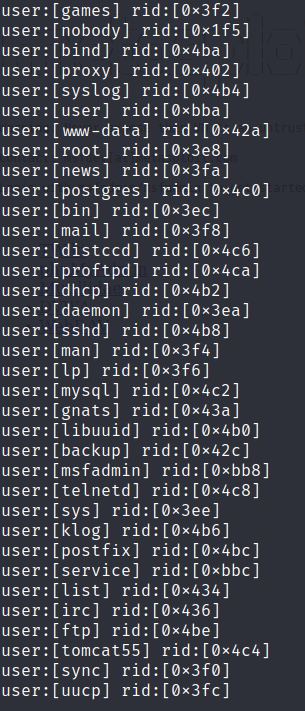
Additionally, enum4linux found all of the users on the host.
Finally, enum4linux also shows us all of the shares that are discoverable.
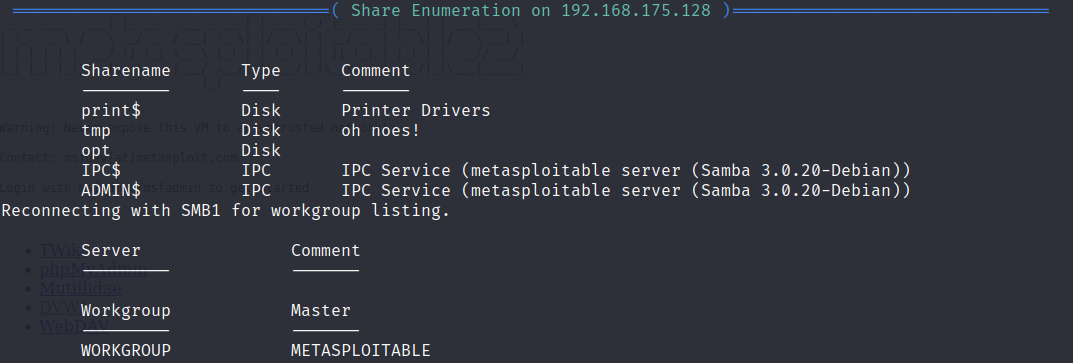
Knowing the user names means that a tester could then initiate a dictionary attack against the SMB services to gain access as one of the users.
Knowing which shares are accessible may allow the tester to then navigate through files that contain information that allows the tester to escalate privileges or pivot to another device on the network.
6. Summary
enum4linux is a great tool to start with when enumerating Windows and Samba services.
A tester or developer could use enum4linux to find out what information is presented publicly and determine if that information is exploitable.
Hopefully, you can use enum4linux during your penetration testing practice on some of the Hack The Box machines or Try Hack Me rooms!
Thanks for reading!
If you have suggestions for what tool to cover next, contact me!