1 . Introduction
2 . My Setup
3 . What is Nikto?
4 . Why use Nikto?
5 . How to use Nikto?
6 . Summary
This post is designed to introduce you to the tool Nikto.

1. Introduction
Welcome to the twentieth blog post of 100 tools in 100 days.
Find Nikto here.
or at the GitHub here
2. My Setup
For running the Nikto tool, I used Kali Linux in a VMware Workstation 16 Player virtualized environment.
For my sample website, I am using the Metasploitable 2 instance running in a VMWare Workstation 16 Player virtualized environment.
3. What is Nikto?
Nikto is a tool used by developers and penetration testers for finding vulnerabilities in web servers.
Nikto is described on its GitHub as a web server scanner that tests against “multiple items, including over 6700 potentially dangerous files/programs, checks for outdated versions of over 1250 servers, and version specific problems on over 270 servers. It also checks for server configuration items such as the presence of multiple index files, HTTP server options, and will attempt to identify installed web servers and software.” Nikto Website
4. Why use Nikto?
As a developer, you could use Nikto as one of your many tools for testing your web presence for vulnerabilities.
As a penetration tester, you could use Nikto to find vulnerabilities that may be potential exploit points for your team.
5. How to use Nikto?
I have set up the Metasploitable 2 DVWA server to mimic a vulnerable web server.
Step 1:
You can read the help menu for Nikto by typing:
nikto -Help
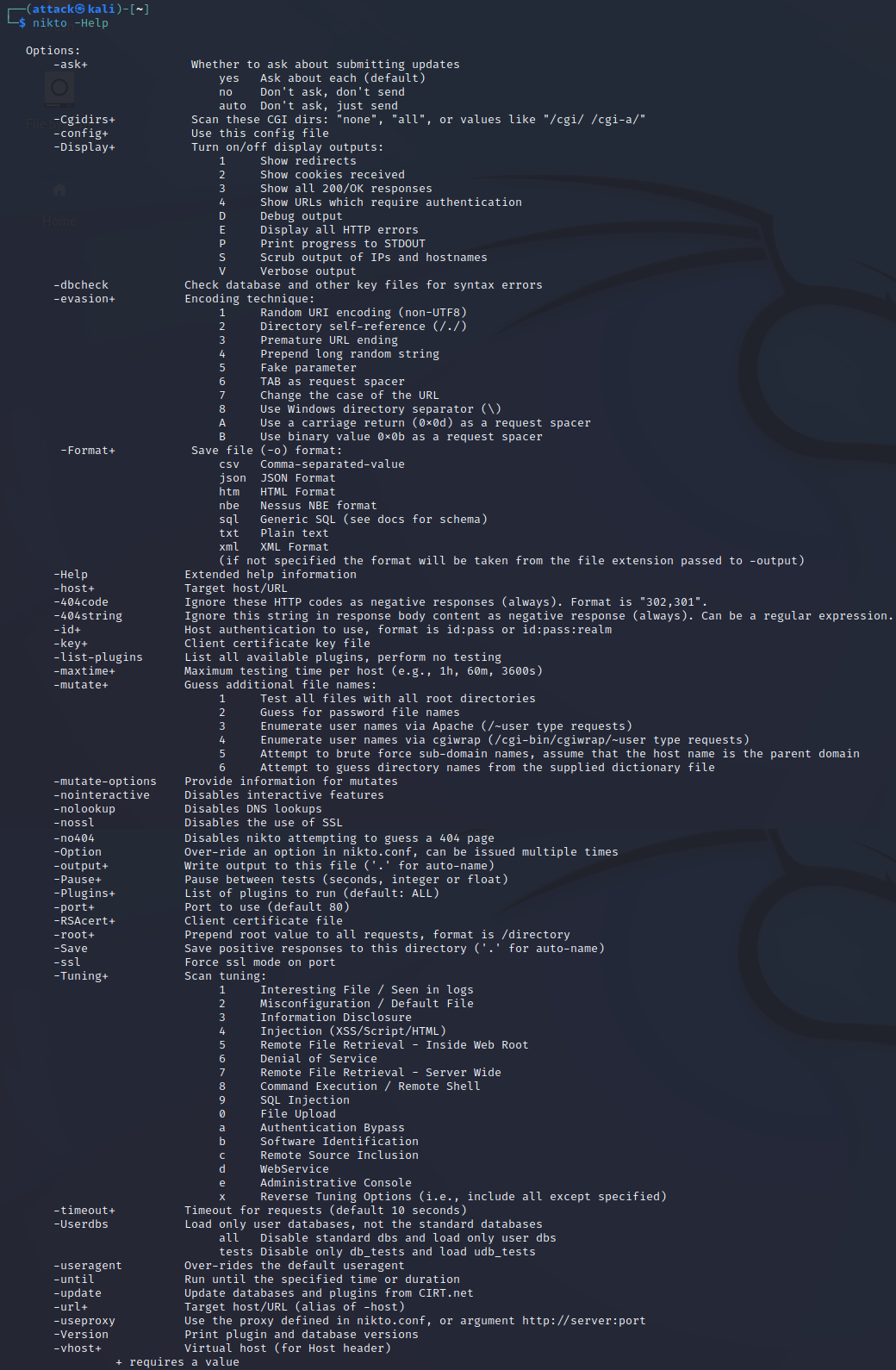
Step 2:
For this exercise, I ran Nikto using default settings against the
Metasploitable 2 server. I used the following command:
nikto -host 192.168.175.128
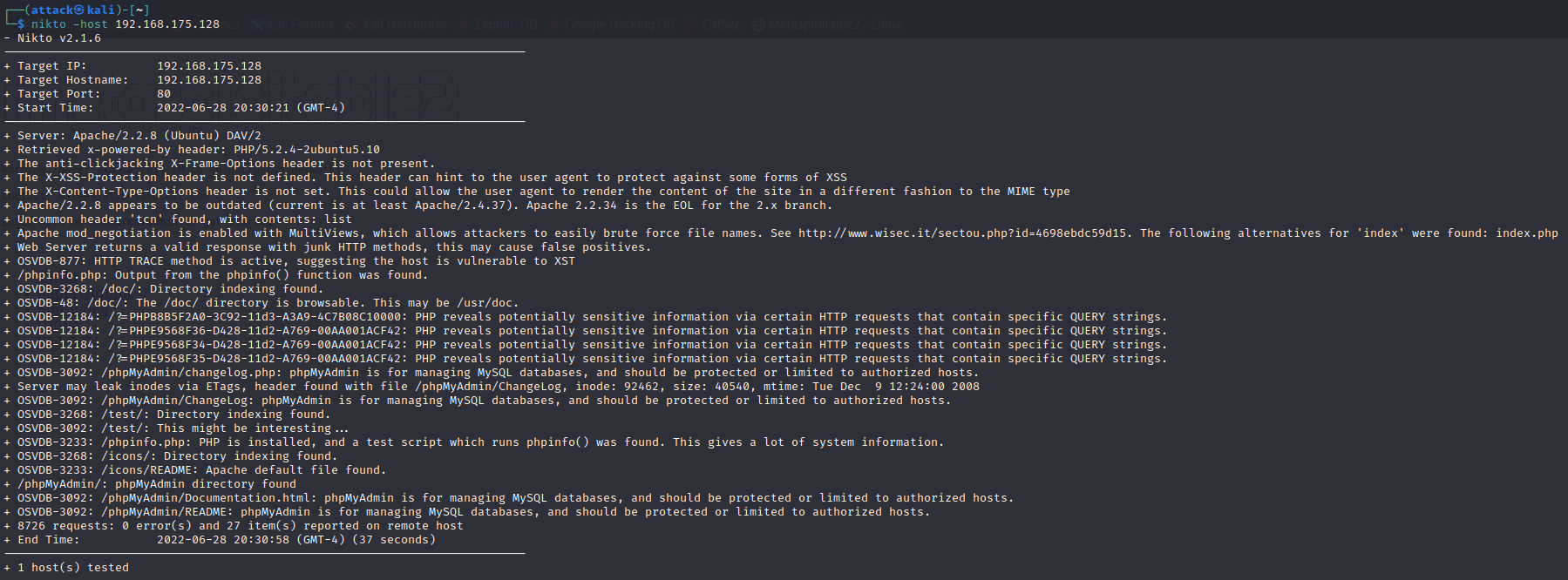
As you can see from the results Nikto found 27 points of interest against the Metasploitable 2 web server.
Some points of vulnerability would likely be the Apache 2.2.8 version. Additionally, Nikto found that the web server likely has PHP vulnerabilities as well as cross-site scripting potential.
6. Summary
Nikto is a great tool to add to a developer or penetration testers kit for scanning a web server for vulnerabilities.
Nikto found some cross-site scripting potential, as well as a vulnerable Apache version, and vulnerable PHP code running on the webserver. All of these vulnerabilities have current exploits that work against them, so they may be considered a higher risk in most environments.
Hopefully, you can add Nikto to your vulnerability testing and use it to find issues that were not known.
Thanks for reading!
If you have suggestions for what tool to cover next, contact me!