1 . Introduction
2 . My Setup
3 . What is Photon?
4 . Why use Photon?
5 . How to use Photon?
6 . Summary
This post is designed to introduce you to the tool Photon.

1. Introduction
Welcome to the eighteenth blog post of 100 tools in 100 days.
Find Photon here.
2. My Setup
For running the Photon tool, I used Kali Linux in a VMware Workstation 16 Player virtualized environment.
For my sample website, I am using the Metasploitable 2 instance running in a VMWare Workstation 16 Player virtualized environment.
3. What is Photon?
We have talked about Open-Source Intelligence (OSINT) in the past. Remember it is information that is easily available to anyone (if they know how to find it).
Photon is an OSINT tool for crawling websites. Crawling is automatically accessing a website and obtaining data from it. Photon crawls a website looking for URLs, emails, social accounts, files, keys, JavaScript, and custom search patterns you create.
4. Why use Photon?
As a penetration tester Photon allows you to find many of the endpoints on a website as well as finds data that may be used in initial footholds such as emails and social media accounts to target during a social engineering attack.
As an investigator, it is beneficial to find as much open-source intelligence as possible to gather evidence for your investigation.
Photon outputs all the URL’s to the data found into easy to read .txt files or you can choose to output the data in a CSV or JSON format as well.
5. How to use Photon?
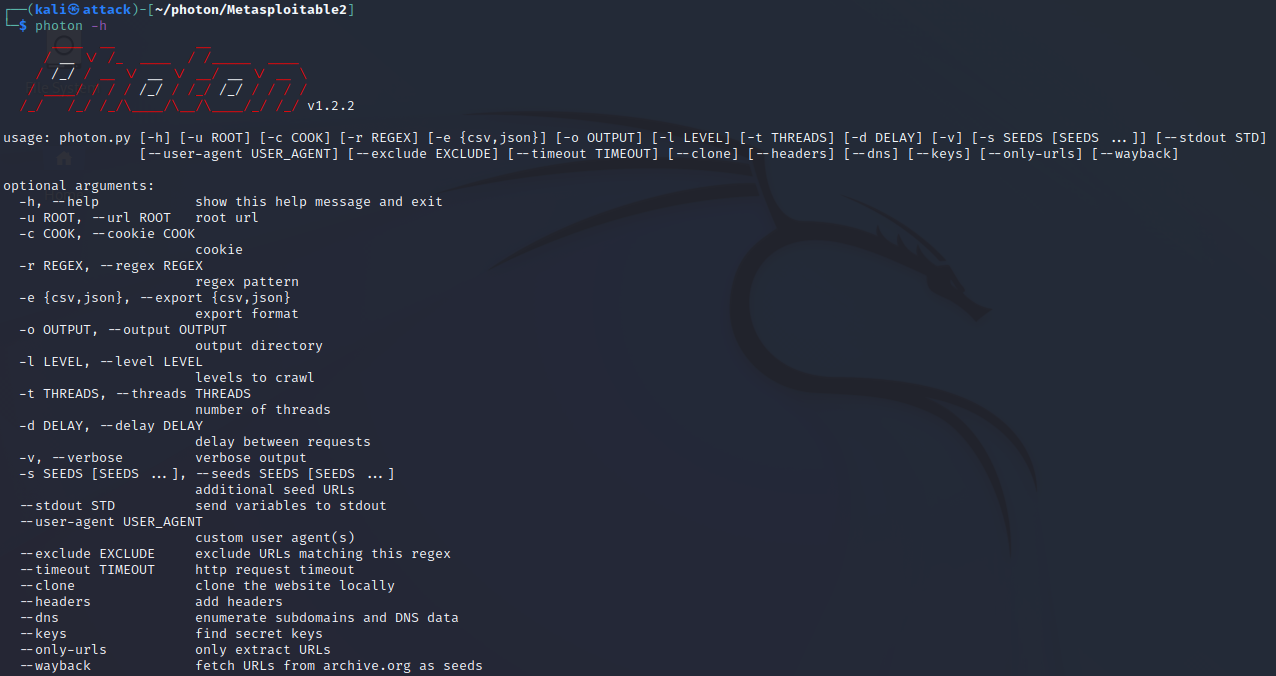
Photon is very easy to use and comes with a help page like many other tools.
Step 1:
To enter the help menu type:
photon -h
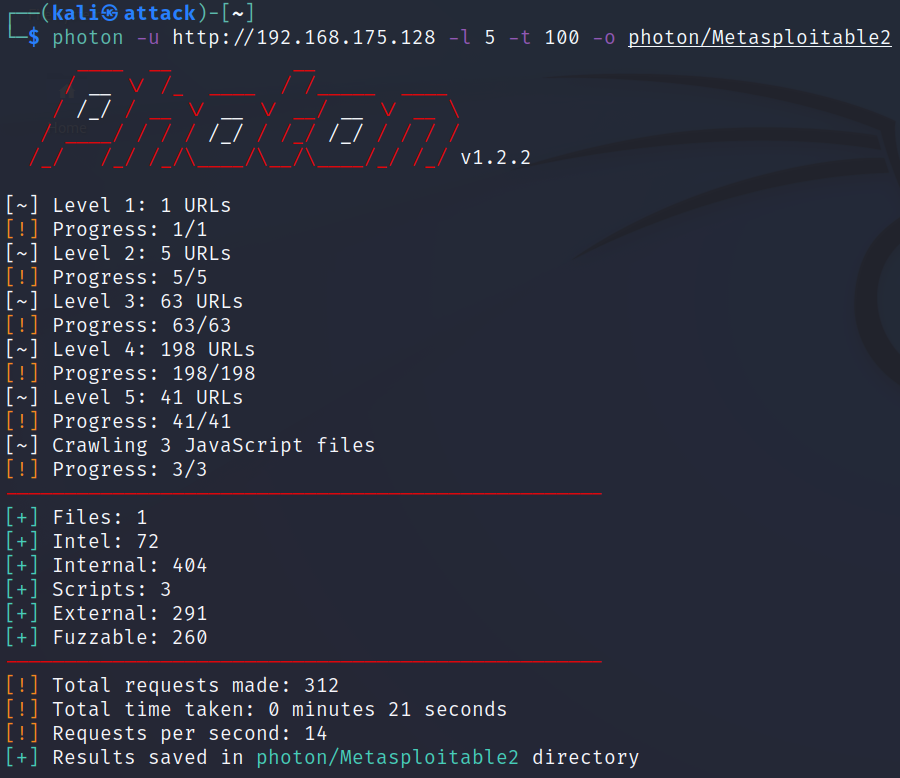
Step 2:
I want to search my Metasploitable 2 website, down 5 levels (directories),
using 100 threads for speed, and output the findings to a folder named
Metasploitable2.
So I would run the following command:
photon -u http://192.168.175.128 -l 5 -t 100 -o /photon/Metasploitable2
As you can see from the output below Photon found:
- 1 file
- 72 pieces of intelligence (emails, social accounts, etc)
- 404 internal addresses
- 3 JavaScripts
- 291 external URLs
- 260 fuzzable pages.
All of the findings are output into .txt files with the URL to the information found.
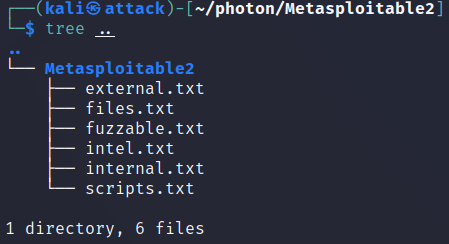
Step 3:
Navigating into each .txt file gives the URL to the information found.
files.txt contains:
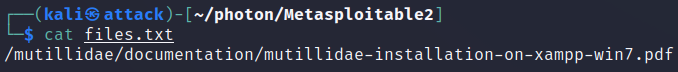
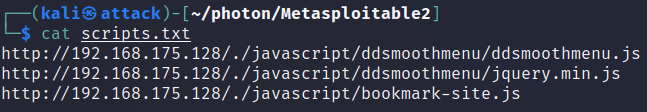
scripts.txt contains JavaScript found:
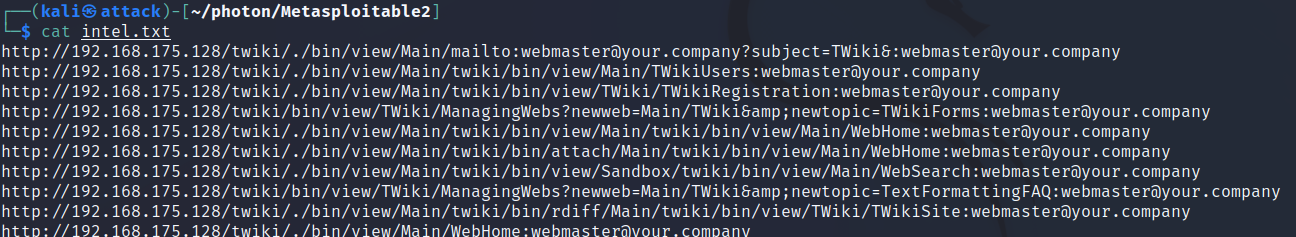
intel.txt contains emails and social accounts found:
6. Summary
Photon allows a user to collect URLs to data that may be helpful to penetration testing or further investigation.
A penetration tester could use this data to pursue social engineering attacks or other attacks to gain access to a target.
An investigator could use this information to create evidence for their investigation.
Thanks for reading!
If you have suggestions for what tool to cover next, contact me!