1 . Introduction
2 . My Setup
3 . What is Hashid?
4 . Why use Hashid?
5 . How to use Hashid?
6 . Summary
This post is designed to introduce you to the tool Hashid.

1. Introduction
Welcome to the seventeenth blog post of 100 tools in 100 days.
Find Hashid here.
2. My Setup
For running the Hashid tool, I used Kali Linux in a VMware Workstation 16 Player virtualized environment.
3. What is Hashid?
First what is hasing:
Hashing is an algorithmic function that takes an input and outputs it as a string of a fixed length. Hashing algorithms are used for verification of the integrity of a file, password, or any input. Sometimes software developers show you the hash output of their downloaded file so you can compare the hash of your download to the original hash of the file from the developer. This ensures that the file has not changed during the download.
Hashid, formerly hash-identifier was created to quickly identify hashed values to their hash algorithm.
4. Why use Hashid?
During penetration testing, an analyst may find a file containing passwords that have been hashed. It would be extremely difficult for an analyst to memorize all of the hashing algorithm qualities of identification, instead using a program like Hashid allows quick identification of hash algorithms.
Identifying the algorithm allows the analyst to run tools that compare the hashed value to pre-computer tables (called rainbow tables) of hashed passwords.
A hash cannot be reversed however, by computing the hash values of every password in a file like rockyou.txt you can quickly compare your found passwords to the rockyou.txt passwords.
Don’t know what rockyou.txt is? Check out the story here.
5. How to use Hashid?
You need a hash value to search. I am using the hash values from this table for the Hashcat tool (more about that tool another time).
In the examples below I used the following hashes:
$DCC2$10240#tom#e4e938d12fe5974dc42a90120bd9c90f
127e6fbfe24a750e72930c220a8e138275656b8e5d8f48a98c3c92df2caba935
Step 1:
Using hashid is very simple. To see the help menu type:
hashid -h
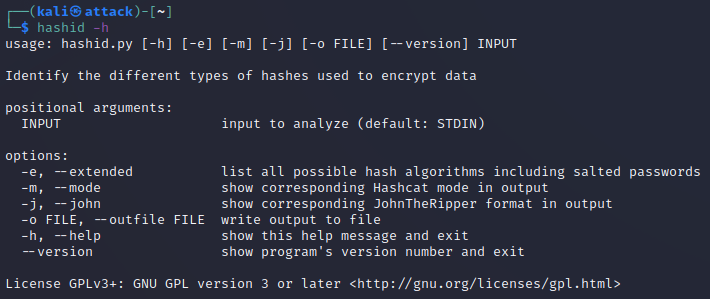
Note: Hashid can accept a hashed value in the command line or you can tell Hashid to analyze the Hash types of a file containing hashes.
Step 2:
I am going to run hashid and I like to keep my hashes between single
quotes. Though it seems like the quotes are ignored.
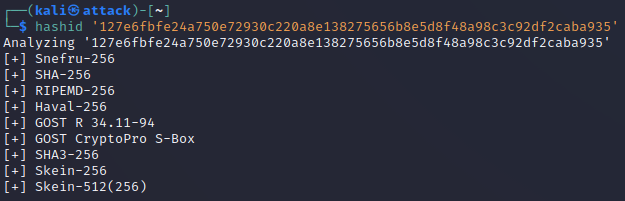
I ran the following comamnd:
hashid '127e6fbfe24a750e72930c220a8e138275656b8e5d8f48a98c3c92df2caba935'
As we can see from the output, likely the hash string is a Snefru-256. I know that the hash string is a SHA-256 because it came from the Hashcat table. So you can see that Hashid does not always report 100% accurately, but SHA-256 is the second suggested algorithm. Therefore, you should always investigate further to determine the exact tool to use next in the process.
Step 3:
Hashid also allows the user to determine the Hashcat and JohnTheRipper
formats to "crack" the original data. (This is used for the rainbow
table style attacks)
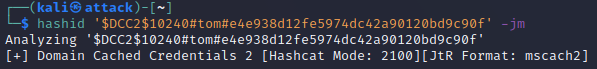
Use the -j -m options when running hashid like below:
hashid '$DCC2$10240#tom#e4e938d12fe5974dc42a90120bd9c90f' -jm
As we can see below in the screenshot the suggested Hashcat mode and JohnTheRipper mode for attacking this hash are output next to the most likely hash algorithm detected.
6. Summary
Hashid is an excellent tool for analyzing the type of Hashing algorithm of a Hashed string of text.
Hashing is generally used to prove integrity. Hashing is also used to obfuscate passwords from plaintext so they cannot be easily readable but can still be accessible from servers to databases during authentication. The hash value during password authentication would prove integrity by comparing the hashed value of the password you input compared to the hashed value of the password stored in a database.
One final note, hashing is not the same as encryption. Encryption can be reversed, whereas hashing cannot be reversed but can be compared to a rainbow table of pre-computed hashed values.
Thanks for reading!
If you have suggestions for what tool to cover next, contact me!