1 . Introduction
2 . My Setup
3 . What is Steghide?
4 . Why use Steghide?
5 . How to use Steghide?
6 . Summary
This post is designed to teach you what the tool Steghide accomplishes and how to use it.

1. Introduction
Welcome to the seventh blog post of 100 tools in 100 days.
In this post and concurrent posts, I will introduce you to a tool in Kali or Parrot Linux.
I will discuss use cases for the tool.
Finally, I will show a quick how-to to get you started using it.
2. My Setup
For running the Steghide tool, I used Kali Linux in a VmWare Workstation 16 Player virtualized environment.
3. What is Steghide?
Steghide is a command line tool that allows a user to hide data or files inside of an image.
Steganography is defined as:
“the art or practice of concealing a message, image, or file within another message, image, or file” - Merriam-Webster.
Find more information about Steghide here.
4. Why use Steghide?
From a malicious standpoint, this is an excellent way to send malicious files or code to a victim.
Steganography is a fun way to send messages within other messages, files, or images.
Steganography in itself is insecure, so do not rely on this method of communication for the secure passing of information.
Please do not use this method to send malicious files or code to anyone.
5. How to use Steghide?
Step 1:
Open your terminal in Kali linux.
Ensure you have steghide installed by typing:
man steghide
This should show you the manual for steghide.
Press q to exit the manual.
Step 2:
steghide is a simple tool but does have peculiar commands that you can
reference in the manual.
For this example, we will need an image and a file to use steghide.
I have chosen a .jpeg image of Neopets called:
neopetsnosteg.jpeg
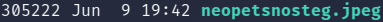
Use the ls command to check the file size:
The file size is 305,222 bytes (298kb approx).
The file size is important as that is the reference we will use after we
have added secret information to the image.
See the picture “neopetsnosteg.jpeg” and a screenshot of the file size below.

Step 3:
We need to create a file to hide within the image.
I created a txt file named "neopetspriortosteghide.txt that contains the
data: "Neopets are the best" using the following command:
echo "Neopets are the best" > neopetspriortosteghide.txt
use the ls command to check the file size:
ls-l
This text file is 21 bytes.
Step 4:
Combining the file "neopetspriortosteghide.txt" into neopetsnosteg.jpeg is
easy.
Run the following command in your terminal:
steghide embed -ef neopetspriortosteghide.txt -cf neopetsnosteg.jpeg -sf
neopetswithsteg.jpeg -p neopets

Congratulations, you have embedded the text file neopetsppriortosteghide.txt into the image neopetsnosteg.jpeg and output the file as neopetswithsteg.jpeg and a passphrase of neopets.
You can verify the image has the embedded file by checking its size using ls -l.
Step 5:
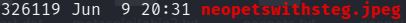
Verify the file size of the output image neopetswithsteg.jpeg
ls -l | grep neopetswithsteg.jpeg
As we can see below the new filesize of the same image is now 326,119 bytes
(318kb approx).
But the image looks exactly the same! <br>
Step 6:
Lets verify our text file really is hidden within the image by extracting it
using steghide.
Run the following command on your embedded image:
steghide extract -sf neopetswithsteg.jpeg -p neopets -xf
neopetsfileextracted

This should have output a file named ‘neopetsfileextracted’ which has the original phrase “Neopets are the best”
Step 7:
Lets check the contents of the file neopetsfileextracted
cat neopetsfileextracted
We can see that our original file contents were indeed hidden within the jpg we created from the original jpg and text file.
6. Summary
This blog post showed you a very brief overview of what Steghide is, and some of its capabilities.
Steghide is a simple tool to perform steganography actions on files, objects, or images.
Please do not hide malicious files within each other. Use this tool for good and use this tool to extract information from files, such as those you find on Hack The Box!
Thanks for reading!
If you have suggestions for what tool to cover next, contact me!