1 . Introduction
2 . My Setup
3 . What is Social-Engineering Toolkit?
4 . Why use Social-Engineering Toolkit?
5 . How to use Social-Engineering Toolkit?
6 . Summary

This post is designed to introduce you to the tool Social-Engineering Toolkit (SET).
1. Introduction
Welcome to the forty-sixth blog post of 100 tools in 100 days.
Find Social-Engineering Toolkit @ GitHub here.
Find TrustedSec website here.
Find the SET User Manual @ GitHub here.
SET was originally created by David Kennedy, the Founder of TrustedSec, and you can find him at:
LinkedIn
GitHub
2. My Setup
For running the Social-Engineering Toolkit tool, I used Kali Linux in a VMware Workstation 16 Player virtualized environment.
For my victim device, I am using Ubuntu in a VMware Workstation 16 Player virtualized environment.
Social-Engineering Toolkit is a framework that allows a penetration tester to create custom attacks (mostly social engineering attacks) to use during a penetration test specifically targeting a person or organization.
Note: this tool is dangerous and should only be used for research in your home lab or by penetration testers with explicit permission.
If you are a penetration tester and have flexible rules of engagement, then SET is a great tool for crafting initial malicious social attacks against employees of the organization.
Using SET is as difficult as using Metasploit. You do have to know how the options function, however, it is also very easy to understand. Plus, if you ever get stuck you can always refer to the user manual located here.
Step 1:
In Kali Linux click the Applications icon and go to number
"13 - Social Engineering Tools"
and select:
"social engineering toolkit (root)".
You will need to enter your password if you are using sudo,
if you are root this should not apply.
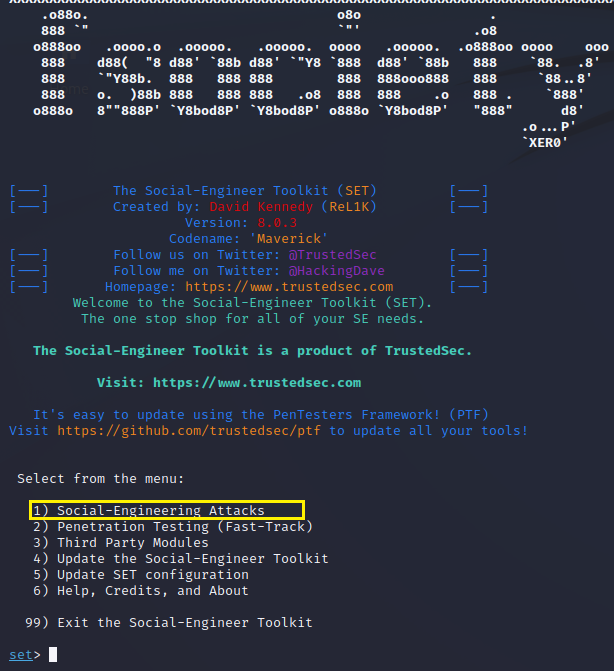
SET loads into a terminal window and creates its own shell that functions very similarly to the Linux shell. It even offers tab auto-complete.
Step 2:
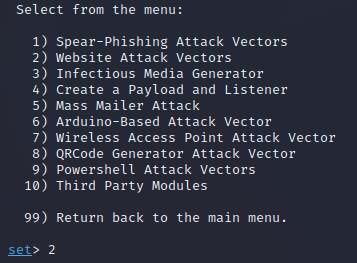
We have multiple options on the main menu, today we are going to focus
on the Social-Engineering Attacks option 1.
type 1 and press enter
Note: If at any time you need to go back to the main menu and there is no option, use Ctrl+C.
Web Attack -> Credential Harvester Example
This example will show you how to perform a credential harvester attack by presenting a fake clone of Google’s login page to the victim.
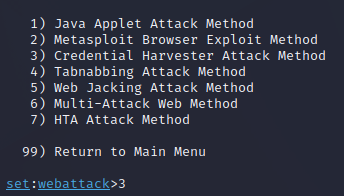
Step 3a:
Enter option 2 to select Website Attack Vectors.
Step 3b:
Enter option 3 to select Credential Harvester Attack Method.
Step 3c:
For simplicity of this example choose option 1 for Web Templates.
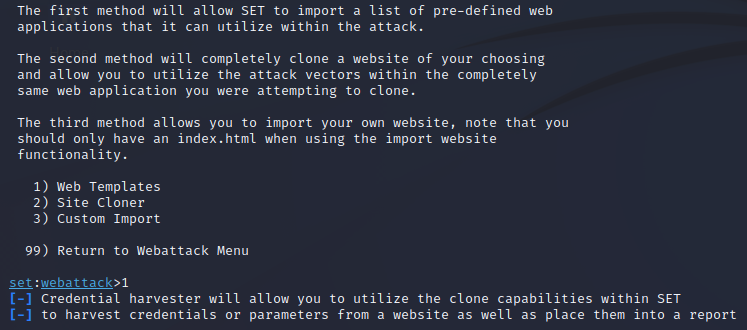
Step 3d:
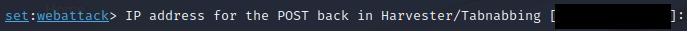
This is where you would enter an IP address for listening to capture
credentials and hosting the page. Since I am working in a close virtual
environment I used my Kali NAT address (default) by hitting enter.
Step 3e:
I chose option 2, Google template for ease of use for this example.
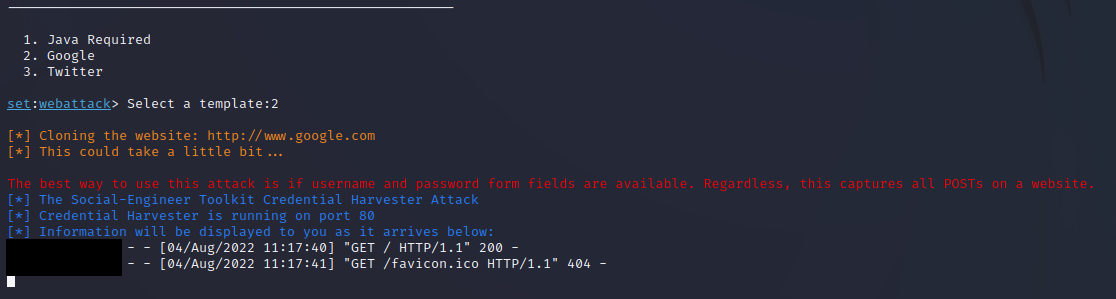
At this point, the website is being hosted at the address chosen in step 3d which for me is kali.ip.address:80.
Step 3f (victim):
On the attack machine, you would want to send this hosted page IP
address in the form of a phishing email, fake website, 'Click here you
won $1,000' style link to the victim.
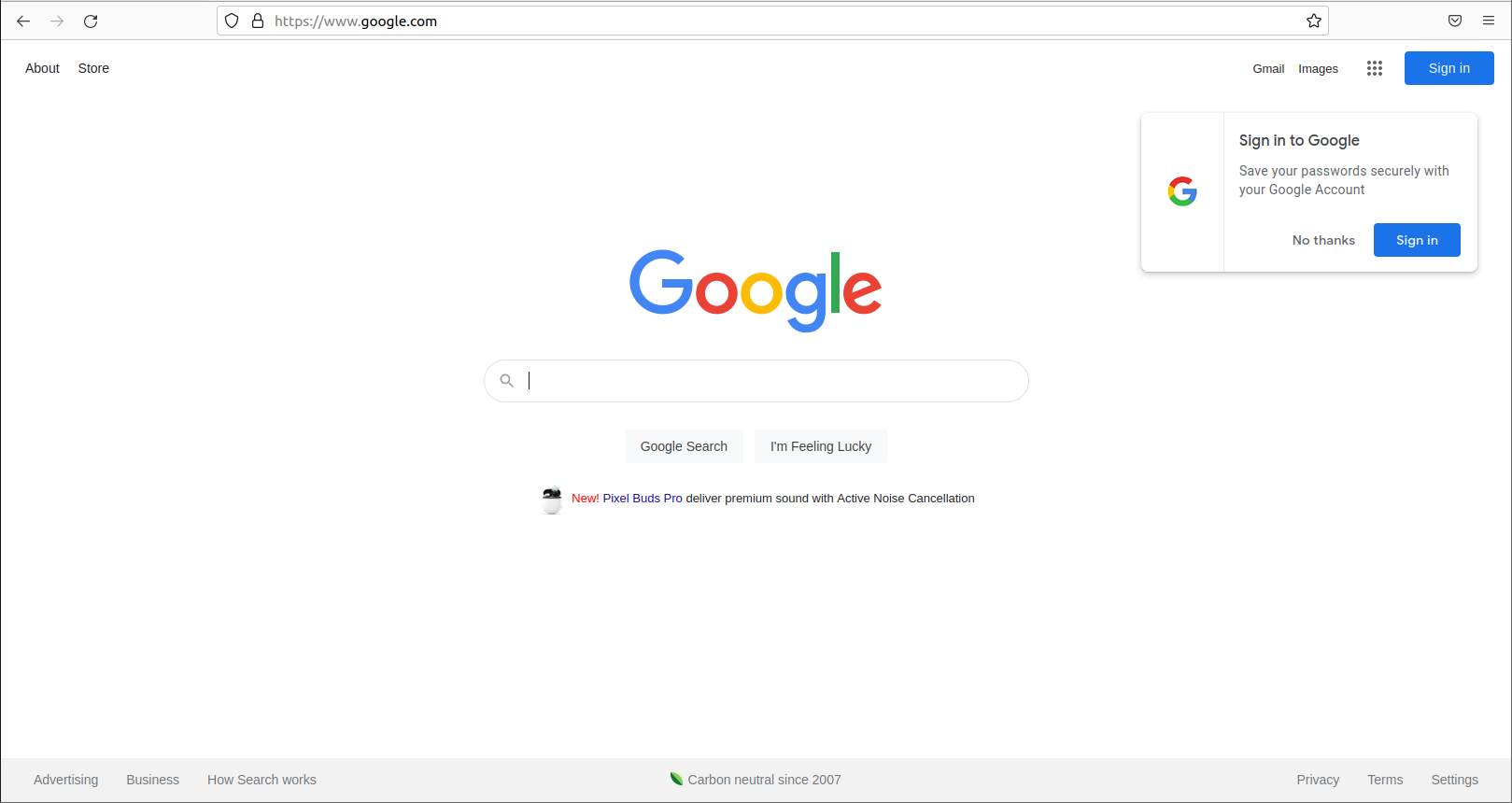
Below is what the victim would see if they clicked the fake link.
I entered a test username and test password and clicked sign in on the
fake Google page.
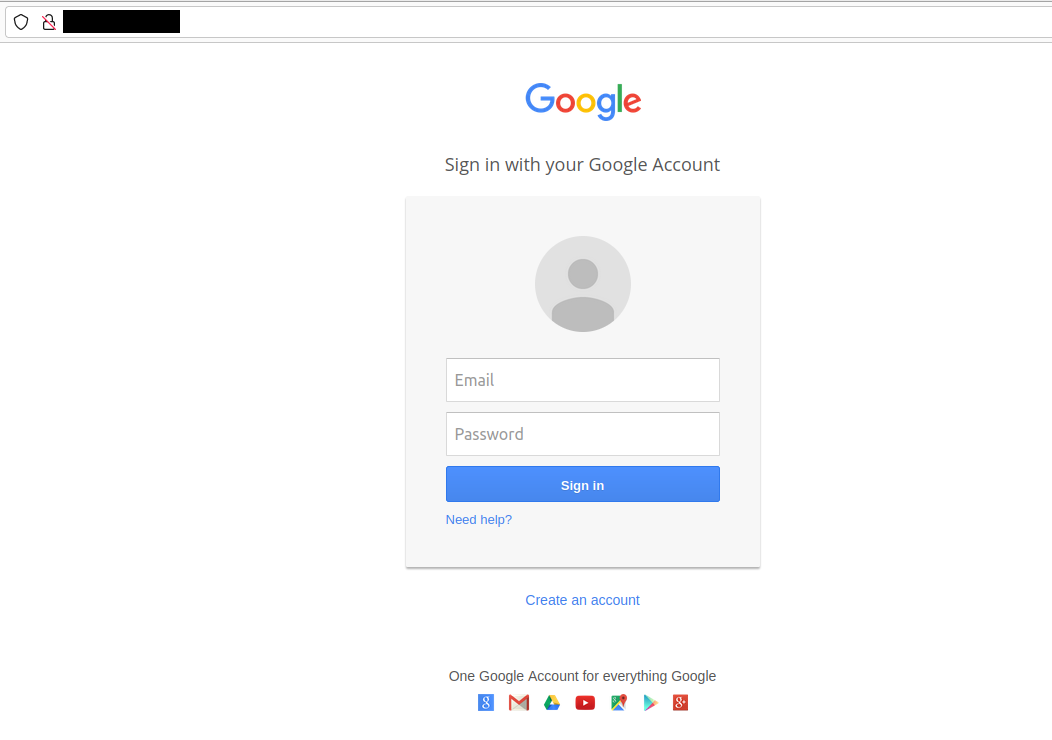
Once the victim enters their login credentials to the fake website the site redirects them to the real site (although not logged in, obviously).
Step 3g:
On the attack machine, the captured data is logged in the SET shell and
also can be saved to an XML report page for retrieval at a later time.
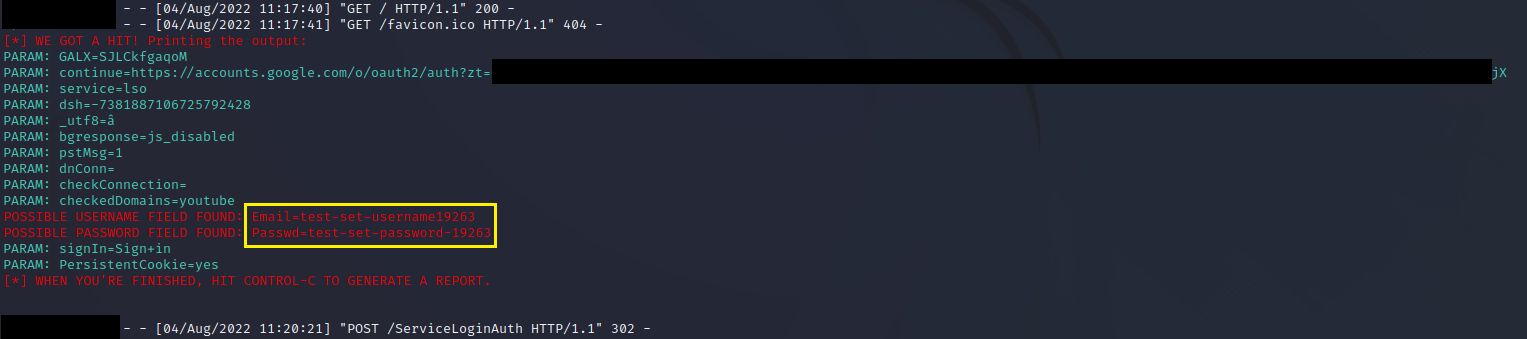
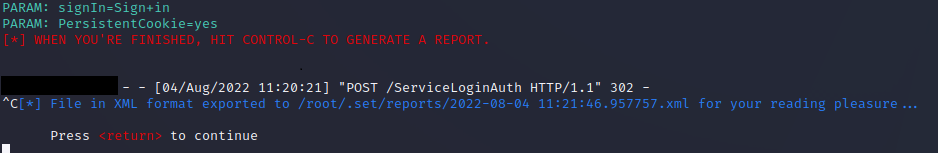
The XML file report looks like this:

This is one of the many examples of how to use SET to create malicious social-engineering attacks against persons or organizations.
###
6. Summary
The Social-Engineering Toolkit (SET) is a tool for crafting social-engineering attacks against people and organizations.
The tool functions in a similar way as Metasploit and allows attackers to create web-based attacks, phishing campaigns, mass mailing campaigns, and many other attack vectors.
Thanks for reading!
If you have suggestions for what tool to cover next, contact me!