1 . Introduction
2 . My Setup
3 . What is pyWhat?
4 . Why use pyWhat?
5 . How to use pyWhat?
6 . Summary
This post is designed to introduce you to the tool pyWhat.
.png)
1. Introduction
Welcome to the forty-third blog post of 100 tools in 100 days.
Find pyWhat @ GitHub here.
pyWhat was created and is maintained by Brandon Skerritt, find him at:
GitHub
LinkedIn
Personal Blog
2. My Setup
For running the pyWhat tool, I used Kali Linux in a VMware Workstation 16 Player virtualized environment.
I used the following PCAP files from Marcelle Lee for analysis:
PCAP File Directory
offshore.pcap
hotel.pcap
evil.pcap
3. What is pyWhat?
pyWhat is a discovery tool that analyzes input such as strings, files, GitHub repositories, and web pages and identifies information found as standard out.
4. Why use pyWhat?
pyWhat can help a security researcher perform a quick analysis on a PCAP file from a network scanner.
Penetration testers may use pyWhat to find leaked data in GitHub repositories or websites of organizations they perform testing on. This is a tool that could be used in the OSINT phase of passive reconnaissance and in the active reconnaissance portion of testing.
5. How to use pyWhat?
Installing pyWhat is easy and requires pip3 from python, if you have been following my posts we installed pip3 previously, but here is the command to install if you need it still:
sudo apt-get install python3-pip
Step 1:
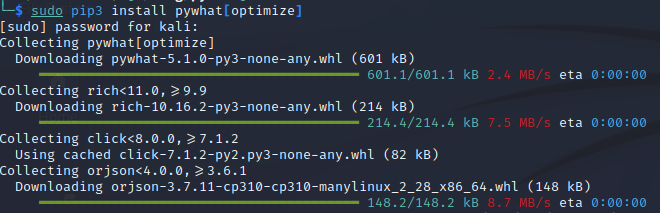
Install pyWhat by entering the following command into your terminal:
sudo pip3 install pywhat[optimize]
Step 2:
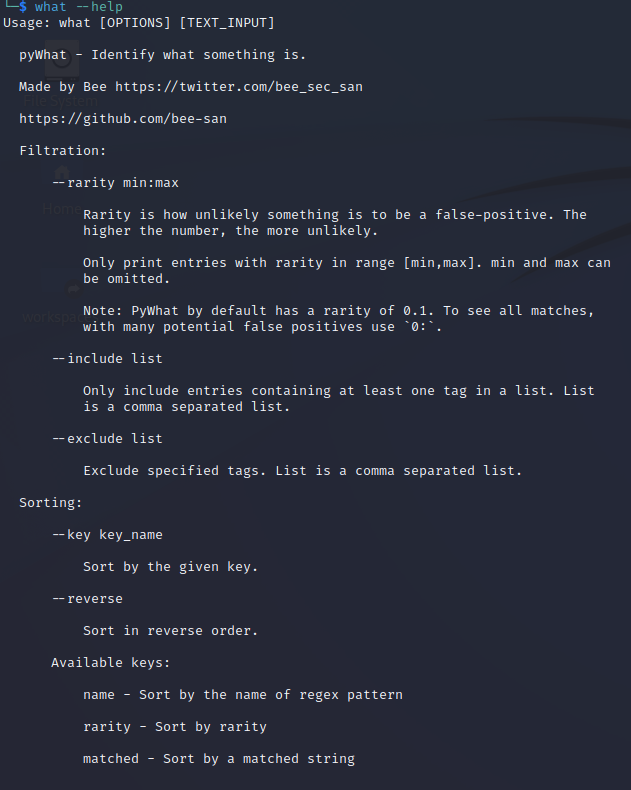
Read the help page for pyWhat by entering the following command:
what --help
Step 3:
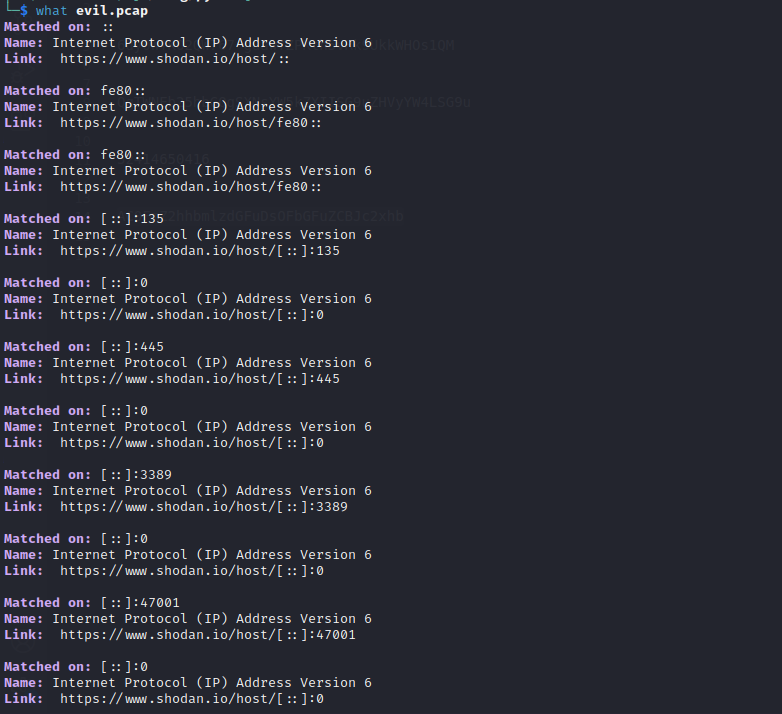
Scanning a PCAP file is easy, enter the following command:
what filename.pcap
Step 4:
Analyzing a string is easy, enter the following command:
what "string_of_text" --format pretty
Using the --format pretty option places found data in a table format.
Though, using this option on a PCAP file does not seem to work
and returns an error.
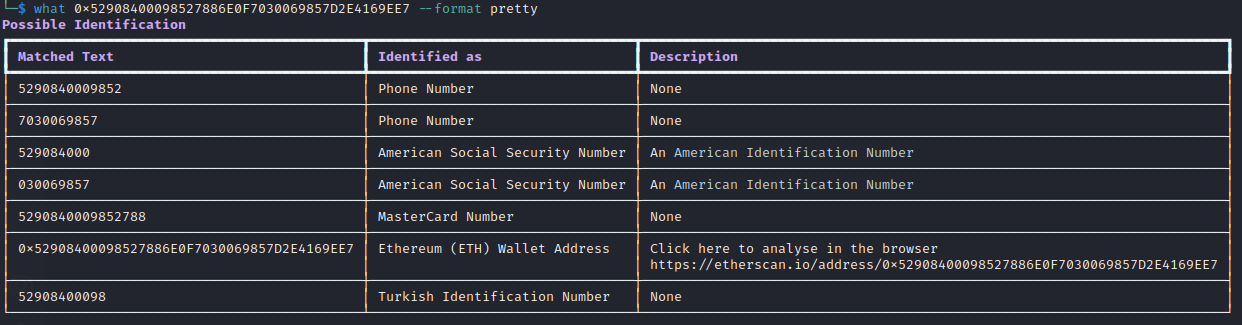
Analyzing the results and determining what may be false positives is important when using pyWhat. pyWhat may be automated but still requires a user to verify data and information extracted, as most tools.
6. Summary
pyWhat is a simple tool for analyzing data and outputting information as to what it believes the information is.
Additionally, pyWhat can analyze PCAP files, other files, GitHub repositories, etc, and find information (secrets) that maybe shouldn’t be available.
I hope you enjoyed this blog post.
Thanks for reading!
If you have suggestions for what tool to cover next, contact me!