1 . Introduction
2 . My Setup
3 . What is WPScan?
4 . Why use WPScan?
5 . How to use WPScan?
6 . Summary
This post is designed to teach you what the tool WPScan accomplishes and how to use it.

1. Introduction
Welcome to the ninth blog post of 100 tools in 100 days.
In this post and concurrent posts, I will introduce you to a tool in Kali or Parrot Linux.
I will discuss use cases for the tool.
Finally, I will show a quick how-to to get you started using it.
2. My Setup
For running the WPScan tool, I used Kali Linux in a VMware Workstation 16 Player virtualized environment.
Additionally, to host a vulnerable WordPress site I used the Try Hack Me room “WordPress: CVE-2021-29447”. I am a daily learner on the Try Hack Me platform and remembered completing this room in the past, so I figured it would be an easy example site to use WPScan on. You can find the room here.
Here is a screenshot of the vulnerable WordPress site from Try Hack Me:
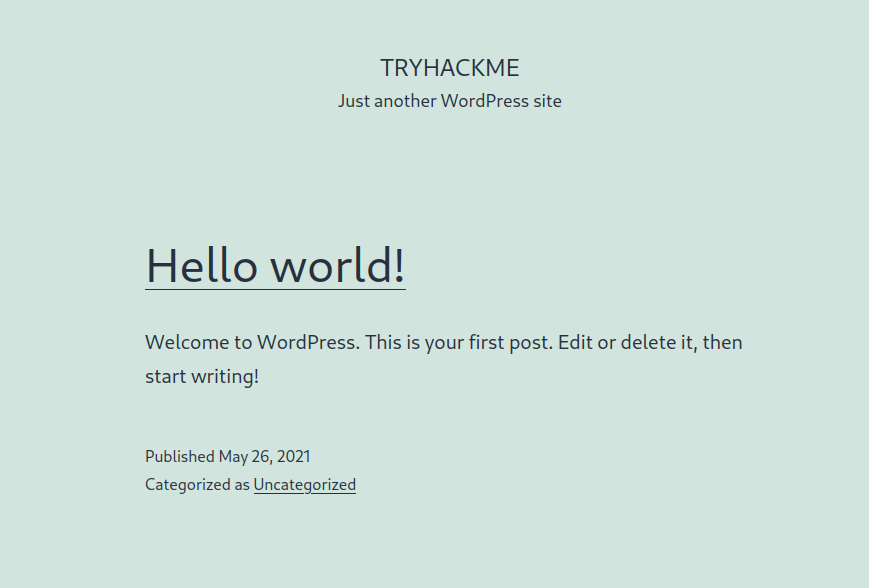
3. What is WPScan?
WPScan is a command line tool that scans WordPress sites for security vulnerabilities.
According to the WPScan website, WPScan uses a database of 28,849 vulnerabilities when scanning sites.
Find more information about WPScan here.
WPScan GitHub here.
4. Why use WPScan?
To check your website for WordPress vulnerabilities.
Perform enumeration of your WordPress site to determine the attack surface area.
Use the WPScan findings to implement hardening methods to prevent vulnerabilities from being exploited.
Use WPScan during penetration testing to find vulnerabilities to gain access to an organization.
Disclaimer:
Please only use WPScan on WordPress sites that you have explicit permission to test.
5. How to use WPScan?
Step 1:
For WPScan to scan for vulnerabilities you will need to register for an
account at https://wpscan.com/.
Once registered navigate to your Profile page in the top right of the site.
You should see your API token and the amount of Daily API Request Limits.
Keep that API key available as you will need it in step 3.
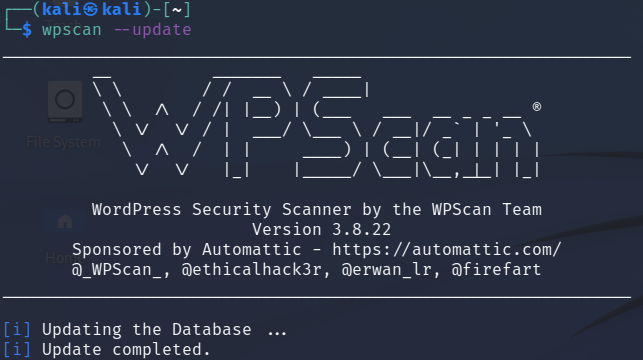
Step 2:
Ensure that the WPScan database is updated before performing a
scan.
Open a terminal and type:
wpscan --update
This will update WPScan and now you are ready to scan your WordPress site.
Step 3:
To scan your WordPress site type:
wpscan --url <INSERT URL HERE> --api-token <INSERT TOKEN HERE>
You will receive output in the terminal screen as to what vulnerabilities and security flaws WPScan has detected.
WPScan also points out interesting findings like directories, headers, files, pages, etc.
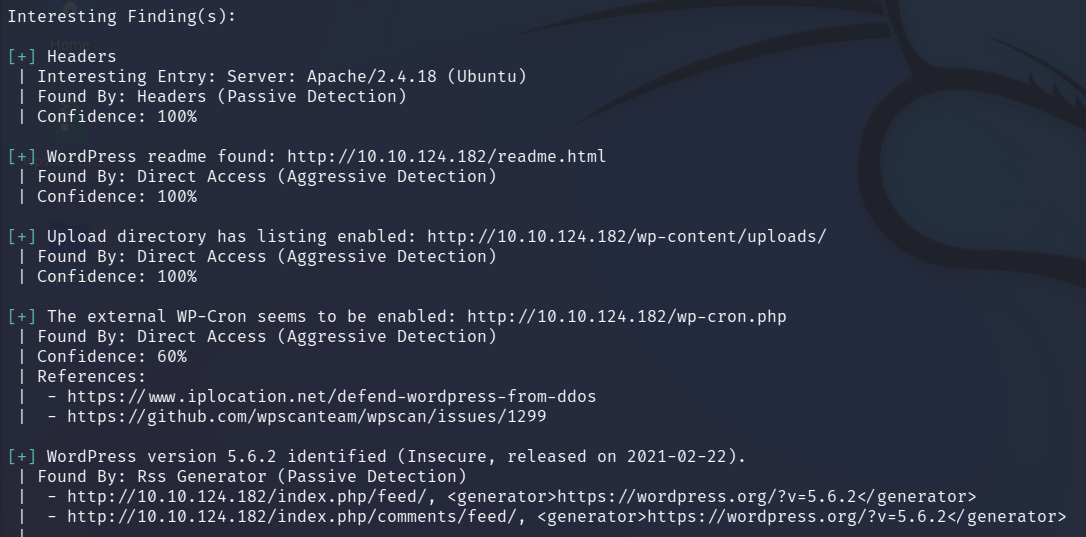
For this example site from Try Hack Me we are looking for the XXE (external
entity injection) vulnerability.
WPScan immediately found the XXE vulnerability and 12 other major issues.
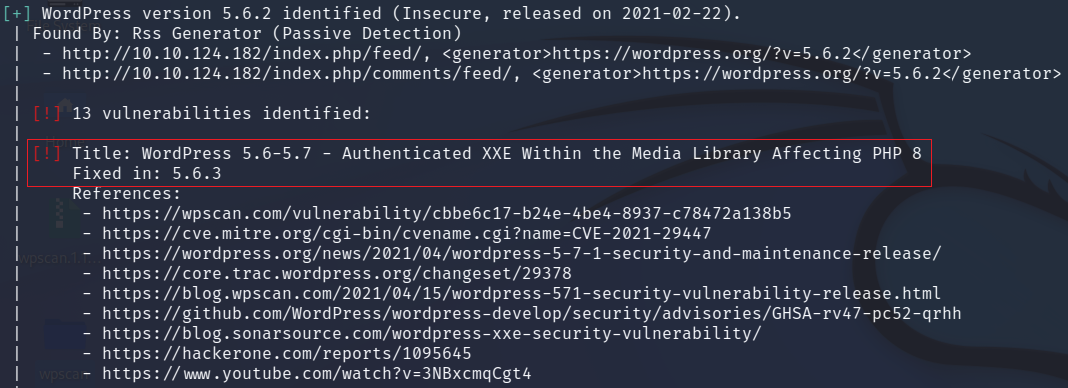
Congratulations You have used WPScan on a WordPress website to detect its vulnerabilities.
6. Summary
This blog post showed you a very brief overview of what WPScan is, and some of its capabilities.
WPScan can help a WordPress owner or developer determine the surface area and vulnerabilities that exist on their WordPress website.
This is not an all-inclusive tool and you should combine WPScan with other web vulnerability scanners to capture a complete picture of the security of your site.
Thanks for reading!
If you have suggestions for what tool to cover next, contact me!