1 . Introduction
2 . My Setup
3 . What is Dirb?
4 . Why use Dirb?
5 . How to use Dirb?
6 . Summary
This post is designed to teach you what the tool Dirb accomplishes and how to use it.
1. Introduction
Welcome to the sixth blog post of 100 tools in 100 days.
In this post and concurrent posts, I will introduce you to a tool in Kali or Parrot Linux.
I will discuss use cases for the tool.
Finally, I will show a quick how-to to get you started using it.
2. My Setup
For running the Dirb tool, I used Kali Linux in a VmWare Workstation 16 Player virtualized environment.
For my victim website, I used the Metasploitable2 server on a VMWare Workstation 16 Player virtualized environment.
- You could use Dirb on Hack The Box rooms and some Try Hack Me rooms if you do not have resources for setting up Metasploitable 2.
3. What is Dirb?
Dirb is a command line web content scanner that enumerates directories and objects using a dictionary style attack.
Find more information about Dirb here.
4. Why use Dirb?
Discovery! Dirb allows a user to discover pages and objects inside of a website.
Dirb allows a developer or pentester to enumerate the directory and objects of a website.
Most importantly this can help developers find pages that are accessible to the public that should not be visible.
Dirb does have some limitations, you shouldn’t expect Dirb to find every directory and object as its search parameters are limited to the default wordlist or wordlist you choose.
Disclaimer:
Dirb scans directories of a website, using this on a website you are not authorized to will create alerts and possible punishment in some jurisdictions. Dirb is an active reconnaisance tool.
5. How to use Dirb?
Step 1:
Open your terminal in Kali linux.
Ensure you have dirb installed by typing:
man dirb
This should show you the manual for dirb.
Press q to exit the manual.
Step 2:
dirb is very easy to use and works quite quickly.
Below I will show you a simple directory / object scan of the
Metasploitable2 server.
dirb http://192.168.175.128 -o metasploitable2.txt -N 404 -r
Note: My Metasploitable2 server is locally hosted at 192.168.175.128 your
address will be different.
Here is a breakdown of the above command:
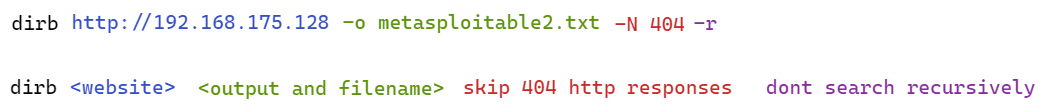
I skipped recursive scanning as I just wanted to get top level directories and objects. You can choose to scan as you wish.
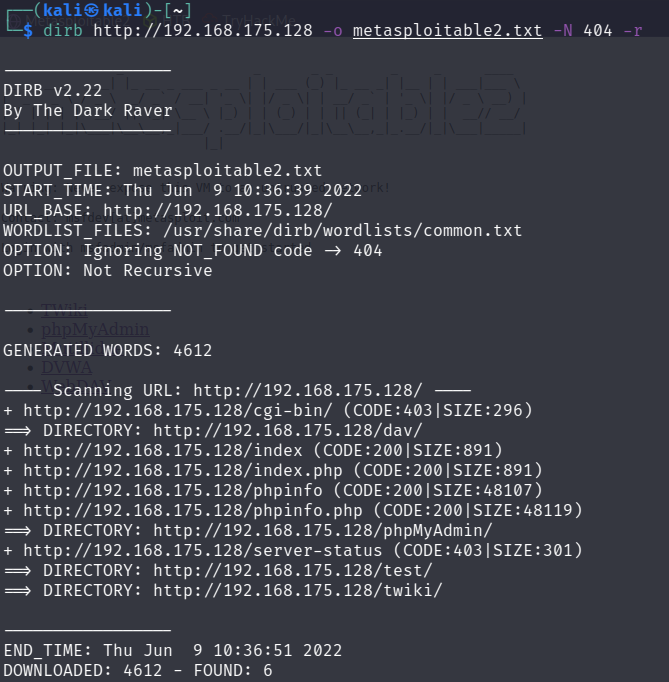
After scanning is completed, my terminal has a standard output that lists all objects and directories that Dirb found during its scan. Again this is limited to the dictionary list used (I used the default common.txt that Dirb uses).
See my output below:
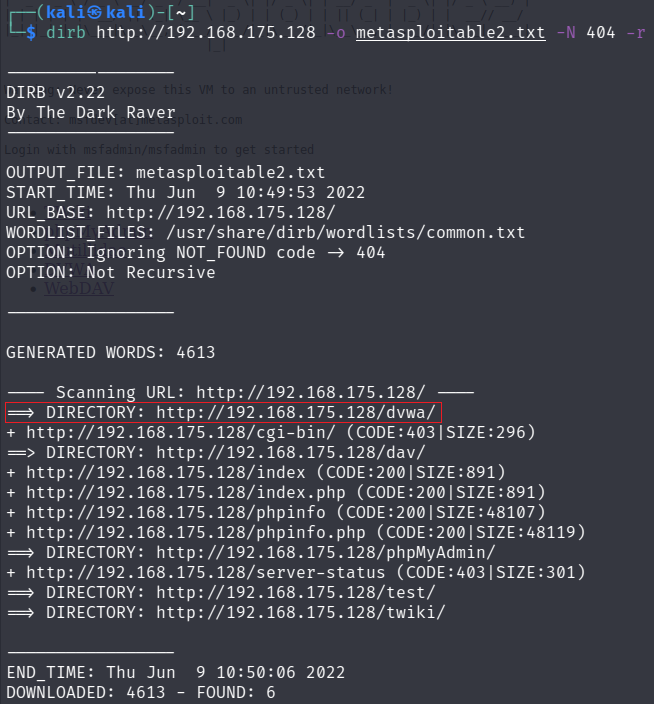
Step 3 (bonus):
If you have used the Metasploitable2 server you know that it comes with the
"Damn-vulnerable-Web-Application" - DVWA. The DVWA is a directory that was
not found by dirb. So I am going to add that search parameter to my dirb
default wordlist located at:
/usr/share/wordlists/dirb/common.txt
You may need root permission to alter this file.
I added dvwa to the top of the file.

Now you can see from my screenshot below the directory dvwa was found immediately.
Step 4 (bonus):
If you wanted to switch the wordlist dirb uses you can add the complete file
path to the dictionary file, to the command immediately following the URL:
dirb http://192.168.175.128 /usr/share/wordlists/notdefault/wordlist.txt -o
metasploitable2.txt -N 404 -r
6. Summary
This blog post showed you a very brief overview of what Dirb is, and some of its capabilities.
Dirb is a quick and easy to use directory and object web scanner.
Dirb does have some limitations, it uses a wordlist for finding directories and objects, as demonstrated when dvwa was not in the default world list, dirb did not find it.
Dirb should only be used on websites where you have permission to perform active reconnaisance.
Go out there and scan your Hack The Box websites for directories!
Thanks for reading!
If you have suggestions for what tool to cover next, contact me!